As DAOs evolve from single-chain collectives to cross-chain governance powerhouses, the promise of seamless interoperability comes with a new set of privacy and security puzzles. Multi-chain DAOs are now able to coordinate voting, treasury management, and proposal execution across multiple blockchain networks. This omnichain approach unlocks efficiency and scale, but it also exposes sensitive data and decision-making processes to new vectors of risk.
Why Cross-Chain DAO Governance Matters
The concept of a cross-chain DAO is simple in theory: allow members to participate in governance activities on any supported blockchain without sacrificing the core principles of decentralization. In practice, this means users can vote, propose changes, or manage assets on Ethereum, Polygon, Solana, or other networks – all under a unified DAO structure. According to Praveen Surendran, this approach leverages the high throughput and unique features of various blockchains while maintaining collective decision-making power.
However, as DAOs expand their reach across chains, they must grapple with increased complexity in both coordination and confidentiality. Sensitive governance data can be exposed during cross-chain messaging or bridge transactions. Member identities may become vulnerable as wallet addresses are linked across ecosystems. Decentralized treasury security becomes far more challenging when assets are scattered among multiple chains.
The Privacy Risks Lurking in Multi-Chain DAO Operations
Let’s break down the main privacy threats facing multi-chain DAOs today:
Key Privacy Risks in Cross-Chain DAO Governance
-

Data Exposure Across Chains: Transmitting governance data between blockchains can reveal sensitive information—such as voting patterns and member identities—to unauthorized parties, increasing the risk of privacy breaches.
-
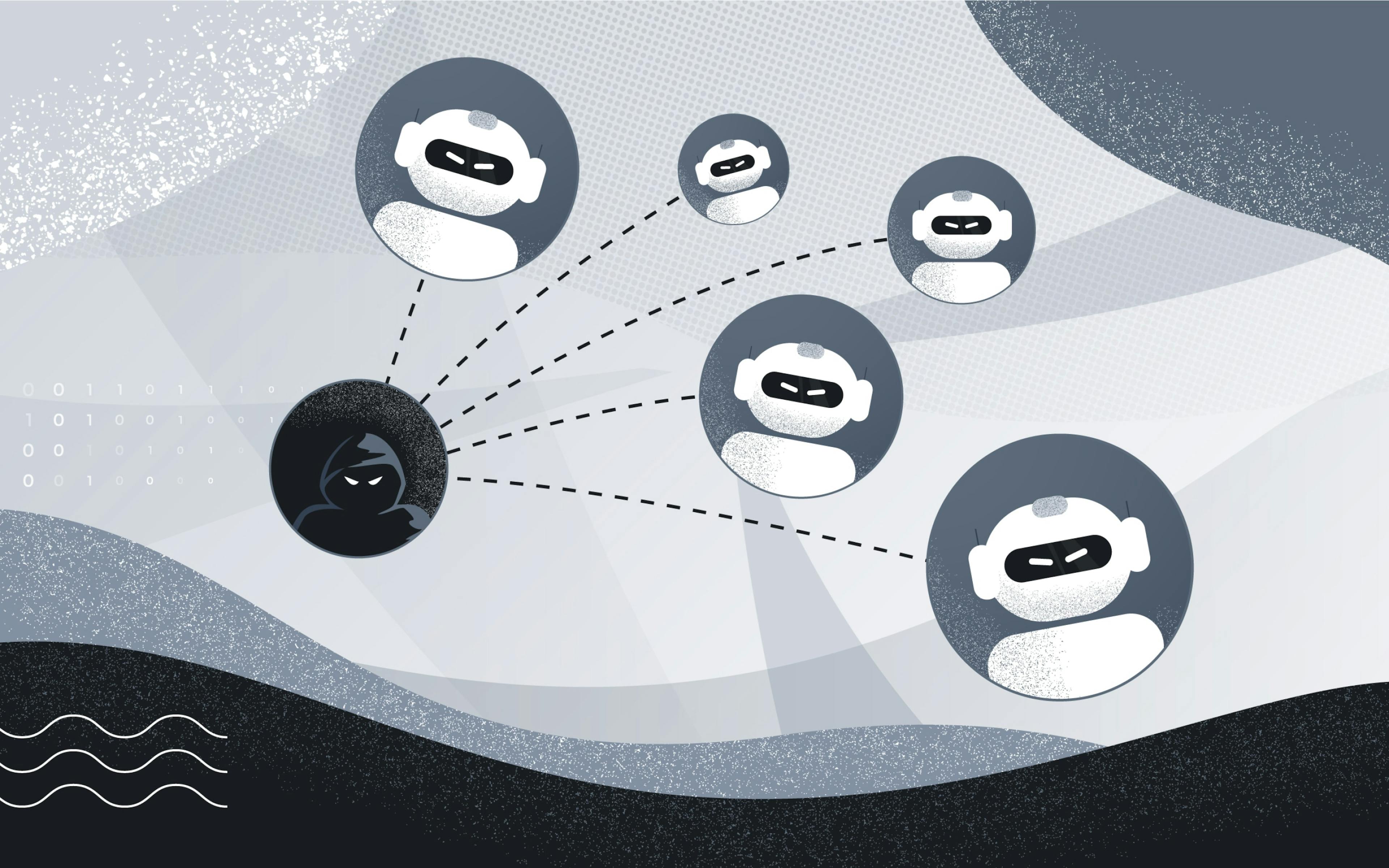
Sybil Attacks via Multiple Chains: Malicious actors may create multiple fake identities across different networks, manipulating voting outcomes and undermining the integrity of DAO governance.
-

Cross-Chain Bridge Vulnerabilities: Bridges that connect blockchains are frequent targets for exploits, which can result in unauthorized access to governance data and assets, posing major privacy and security threats.
-
Inconsistent Privacy Standards: Different blockchains may implement varying levels of privacy protection, leading to potential data leaks when information moves between chains.
-
Traceability of Multi-Chain Activities: Linking wallet addresses and activities across chains can make it easier to deanonymize DAO participants, exposing their governance behavior and holdings.
Data Exposure: Voting records and proposal discussions transmitted between chains can leak member preferences or reveal coalition-building strategies to external observers or adversaries.
Sybil Attacks: The ability for malicious actors to create multiple identities across different blockchains makes it easier to manipulate votes or game reputation systems. Even sophisticated decentralized identity solutions must contend with fragmentation and lack of universal standards.
Bridge Vulnerabilities: Cross-chain bridges are notorious for security flaws that can lead not only to asset theft but also unauthorized access to sensitive governance data. As highlighted by dxtalks.com, bridges remain a major weak point in multi-chain architectures.
Pioneering Solutions for Multi-Chain DAO Privacy
The good news is that the privacy community is rapidly innovating solutions tailored for omnichain DAO operations:
- Zero-Knowledge Proofs (ZKPs): Protocols like zkFi allow DAOs to verify votes or transactions without revealing underlying data – preserving both regulatory compliance and member anonymity.
- Trusted Execution Environments (TEEs): Platforms such as TrustCross use hardware-based enclaves for confidential processing of proposals and votes during cross-network transmission.
- Decentralized Identity Verification: Tools like BrightID help prevent Sybil attacks by ensuring each participant is unique while keeping their real-world identity private.
- Secure Messaging Protocols: Solutions like LayerZero enable trustless communication between blockchains without exposing message contents to intermediaries.
- Fine-Grained Access Control: Systems such as FACOS empower DAOs to tightly regulate who can view or interact with specific governance data on each chain.
The New Standard: Confidential Omnichain Governance
This new era demands that every cross-chain DAO founder consider privacy not as an afterthought but as a foundational requirement. Projects like COTI are setting benchmarks by building enterprise-grade confidential voting infrastructure atop Ethereum Layer 2 networks (syncra.xyz). Meanwhile, research into dual-NFT architectures is enabling flexible separation between identity verification and transaction privacy (arXiv.org). These innovations point toward a future where multi-chain DAO privacy is both robust and user-friendly.
As multi-chain DAOs scale, the challenge is no longer just technical interoperability but the holistic protection of member privacy and governance integrity. The next generation of cross-chain DAO governance must take a layered approach, combining cryptographic techniques, decentralized identity, and operational best practices to ensure that sensitive data is never the weakest link.
Top Privacy-Preserving Tools for Multi-Chain DAOs
-

COTI – A privacy-focused Ethereum Layer 2 blockchain enabling confidential governance and private voting for DAOs, with enterprise-grade privacy features.
-

Oasis Privacy Layer – Provides secret voting and configurable privacy for DAO governance, helping protect member identities and voting patterns across chains.
-
zkFi Protocol – Integrates zero-knowledge proofs (ZKPs) to facilitate privacy-preserving, regulation-compliant transactions and voting across multi-chain protocols.
-
BrightID – A decentralized identity verification platform that prevents Sybil attacks by ensuring unique, anonymous participation in DAOs across multiple blockchains.
-

LayerZero – A trustless interoperability protocol that secures cross-chain messaging, minimizing data exposure and privacy risks during DAO governance operations.
-

FACOS – Implements fine-grained access control for DAOs, allowing precise management of who can access sensitive governance data across blockchains.
-

TrustCross – Utilizes Trusted Execution Environments (TEEs) for confidential processing of governance data in cross-chain DAO operations.
Zero-Knowledge Proofs (ZKPs) are at the heart of this transformation. By enabling on-chain actions, like voting or treasury movements, to be verified without exposing underlying details, ZKPs allow DAOs to maintain transparency for results while safeguarding individual choices. Projects such as zkFi and COTI are pioneering these applications, making it possible for even large-scale DAOs to operate confidentially across networks. For a deeper dive into how COTI’s Layer 2 solutions are influencing this space, see syncra.xyz.
Trusted Execution Environments (TEEs) offer another critical layer by running sensitive computations within hardware-protected enclaves. This means that even if a node or bridge is compromised, confidential proposals and votes remain shielded from outside eyes. The TrustCross platform exemplifies how TEEs can be woven into cross-chain infrastructure to preserve privacy without sacrificing speed or usability.
The issue of decentralized identity cannot be overstated in this context. Without robust Sybil resistance that does not compromise anonymity, cross-chain DAO governance will always be vulnerable to manipulation. Solutions like BrightID and dual-NFT models, where one NFT proves uniqueness and another secures transaction privacy, are pushing the boundaries here (arXiv.org). Decentralized identity frameworks also enable members to carry credentials and reputation seamlessly across chains without leaking personal data.
Best Practices for Secure Omnichain DAO Operations
No privacy solution exists in isolation; effective protection comes from integrating multiple strategies at both protocol and organizational levels. Here are some actionable steps every multi-chain DAO should consider:
- Adopt secure messaging protocols: Use trustless bridges and frameworks like LayerZero to ensure encrypted communication between chains.
- Implement fine-grained access control: Restrict governance data visibility based on role, chain, or proposal sensitivity using systems like FACOS.
- Diversify bridge infrastructure: Avoid single points of failure by leveraging multiple audited bridges for asset and data transfers (dxtalks.com).
- Pursue regular audits: Engage with security researchers to test both smart contracts and off-chain processes for privacy leaks.
- Cultivate a culture of confidentiality: Train community members on OPSEC best practices around wallet management and public disclosures.
Looking Ahead: The Future of Multi-Chain DAO Privacy
The road ahead will see even more sophisticated attacks targeting cross-chain DAOs, but also more powerful defenses. As decentralized treasury security becomes mission-critical for billion-dollar organizations, expect further innovation in omnichain DAO solutions that blend usability with ironclad privacy guarantees. The integration of configurable privacy layers like those pioneered by Oasis Protocol will give communities granular control over what remains private versus public during each phase of governance.
The bottom line? True decentralization means not just distributing power but also protecting every participant’s right to confidential engagement, no matter how many chains your DAO spans. By proactively embracing advanced cryptography, decentralized identity standards, and operational rigor today, DAOs can build resilient communities ready for tomorrow’s challenges in an increasingly interconnected blockchain world.