Securing cross-chain actions is now mission-critical for DAOs with multi-chain exposure. The rise of Maximal Extractable Value (MEV) attacks and the growing sophistication of on-chain adversaries have made privacy and asset protection non-negotiable. In 2025, the landscape is shifting fast: seamless cross-chain bridges like Mantabridge are leveraging zero-knowledge cryptography, while MEV mitigation strategies are maturing beyond their Ethereum roots.
Why Cross-Chain Actions Expose DAOs to MEV
DAOs thrive on transparency, but public ledgers are double-edged swords. Every treasury move, governance action, or asset transfer is visible to anyone watching the mempool. MEV bots exploit this by front-running trades, sandwiching swaps, or reordering transactions for profit. While Ethereum has seen over $1.1B in MEV activity in 2024 (PANews), Solana and emerging chains are quickly catching up – and when DAOs operate across multiple blockchains, the attack surface multiplies.
Cross-chain MEV is especially pernicious because it amplifies arbitrage opportunities and inflates transaction costs (CoW DAO). For DAOs moving assets between chains or executing multi-step governance proposals, a single leak can mean significant value loss or strategic exposure.
MEV Protection Strategies for DAOs
Essential Tools for MEV Protection in Cross-Chain DAOs
-

Flashbots Protect — A private mempool service on Ethereum that shields transactions from MEV bots by keeping them confidential until finalized, reducing the risk of front-running and sandwich attacks.
-

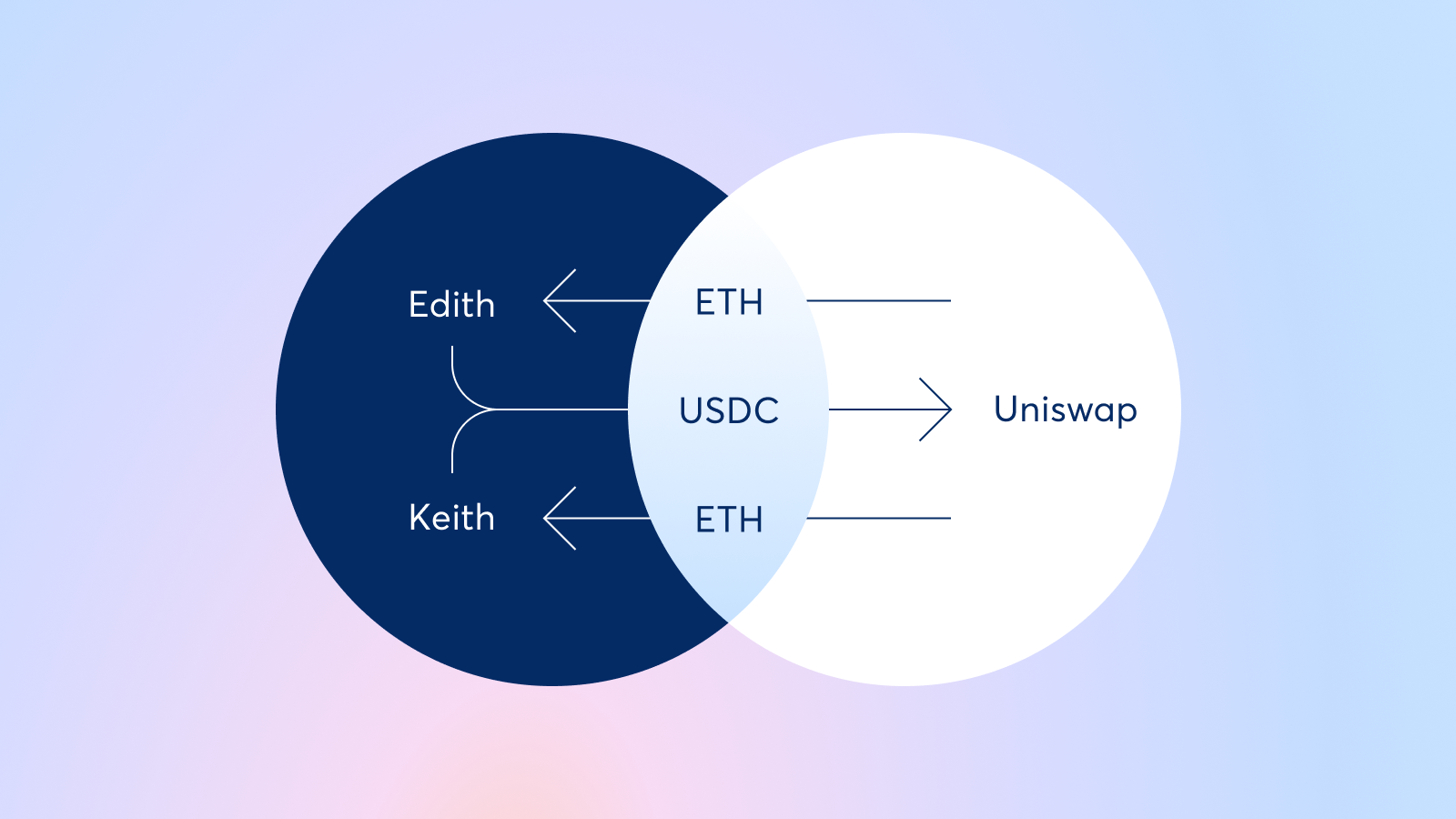
CoW Swap — Utilizes batch auction mechanisms to aggregate and execute multiple transactions simultaneously, neutralizing MEV exploits by removing transaction ordering advantages.
-
Hashflow — Enables bridgeless cross-chain swaps with zero slippage and MEV-protected trades using a request-for-quote (RFQ) model, safeguarding trades from MEV extraction across networks.
-
MantaBridge — The leading cross-chain privacy bridge for 2025, integrating zero-knowledge cryptography to enable confidential, seamless multi-chain transfers and enhance MEV resistance.
-

SurferMonkey Protocol — Implements zero-knowledge proofs to enable decentralized, anonymous blockchain intercommunication, protecting DAO treasury actions from MEV and censorship threats.
Fortunately, new tools give DAOs a fighting chance against MEV predators:
- Private Mempools: Submitting transactions through private relays (like Flashbots Protect) keeps pending actions hidden until finalized. This prevents bots from sniffing out intent and gaming the order flow (Investing Haven).
- Batch Auctions: Protocols such as CoW Swap aggregate orders and settle them simultaneously. This batch execution neutralizes front-running by making transaction order irrelevant to outcome (CoW DAO).
- Bridgeless Cross-Chain Swaps: Solutions like Hashflow use an RFQ model with off-chain pricing and on-chain settlement to eliminate slippage and protect trades from MEV extraction (Consensys Blog).
The Role of Zero-Knowledge Proofs in Confidential Treasury Management
If your DAO’s treasury moves can be observed, so can your risk posture – making you a target not just for traders but also for governance attacks. Zero-knowledge proofs (ZKPs) offer a powerful shield here. With ZKPs, DAOs can prove ownership or execute transfers without revealing sensitive details like amounts or counterparties.
Mantabridge stands out as the first bridge in 2025 to natively support zero-knowledge cryptography for seamless multi-chain transfers (paragraph. com). Meanwhile, protocols such as SurferMonkey demonstrate how ZKPs enable decentralized yet anonymous blockchain intercommunication – crucial for confidential voting or treasury management across chains.
Confidential DAO Asset Management Workflows Using ZKP Bridges
-

MantaBridge: The leading cross-chain privacy bridge for 2025, MantaBridge enables DAOs to transfer assets across multiple blockchains with zero-knowledge proof (ZKP) protection. This ensures transaction details and treasury balances remain confidential, mitigating MEV risks and safeguarding sensitive treasury operations.
-

SurferMonkey Protocol: SurferMonkey leverages ZKPs to facilitate anonymous, decentralized inter-chain communication. DAOs can execute asset transfers and governance actions across chains without exposing transaction metadata, effectively shielding treasury movements from MEV attacks and public scrutiny.
-
CoW Swap Batch Auctions: By integrating with ZKP-enabled bridges, DAOs can use CoW Swap’s batch auction mechanism to aggregate and settle cross-chain treasury actions privately. This workflow prevents transaction reordering and front-running, while ZKPs ensure the confidentiality of the underlying asset movements.
-
Hashflow Bridgeless Cross-Chain Swaps: Hashflow offers MEV-protected, bridgeless cross-chain swaps using an RFQ model. When combined with ZKP-enabled bridges, DAOs can securely execute confidential treasury swaps between chains, with pricing and settlement handled off-chain to avoid MEV exploitation.
-

Private Mempools via Flashbots Protect: DAOs managing assets across chains can route sensitive transactions through Flashbots Protect’s private mempool in conjunction with ZKP bridges. This approach keeps transaction details hidden until finalization, reducing the risk of MEV and maintaining treasury confidentiality.
Navigating Regulatory Implications of Privacy Tools
The regulatory landscape is evolving alongside these technologies. As highlighted by James Grimmelmann’s research, legal scrutiny around MEV mitigation is increasing – especially regarding anti-money laundering (AML) compliance and fair market access. For DAOs, balancing privacy with auditability will be an ongoing challenge as frameworks mature.
Pragmatically, DAOs should prioritize modular privacy: keep critical treasury moves confidential while retaining the ability to selectively disclose for audits or regulatory review. Zero-knowledge asset management systems can support this by offering verifiable proofs of solvency or transaction validity without exposing granular details. As these tools become more accessible, expect a new baseline for cross-chain treasury privacy in 2025, one where confidential DAO asset management is not just possible but expected.
Actionable Steps for Secure Multi-Chain Governance
To future-proof your DAO’s cross-chain operations, consider the following pragmatic steps:
Checklist for Securing Cross-Chain DAO Actions
-
Integrate Private Mempool Services: Use established solutions like Flashbots Protect on Ethereum to submit sensitive transactions privately and shield them from MEV bots.
-
Utilize Batch Auction Platforms: Execute trades on platforms such as CoW Swap, which aggregate multiple orders and neutralize transaction ordering attacks.
-
Adopt Cross-Chain MEV-Protected Protocols: Leverage protocols like Hashflow for bridgeless, MEV-protected swaps using RFQ models and professional market makers.
-

Implement Zero-Knowledge Proof-Based Bridges: Use privacy bridges such as MantaBridge to facilitate confidential, zero-knowledge cross-chain treasury transfers.
-

Deploy Decentralized, ZKP-Enabled Treasury Protocols: Explore protocols like SurferMonkey for anonymous, censorship-resistant treasury management using zero-knowledge proofs.
-
Regularly Audit Cross-Chain Operations: Conduct security audits of smart contracts and cross-chain bridges with reputable firms to identify and mitigate vulnerabilities.
-

Monitor Regulatory Developments: Stay updated on MEV and privacy-related regulations impacting DAOs to ensure ongoing compliance and risk mitigation.
First, integrate private mempool solutions into your transaction workflows, especially for large or strategically sensitive moves. Next, leverage batch auctions and off-chain pricing models where available to reduce MEV exposure on swaps and trades. For cross-chain transfers and governance actions, opt for bridges like Mantabridge that natively support zero-knowledge cryptography, this ensures both confidentiality and composability across ecosystems.
Don’t overlook education and process: train contributors on best practices around transaction privacy, operational security, and the nuances of MEV risk. Use simulation tools to stress-test your DAO’s processes under different attack scenarios. Regularly audit both smart contracts and off-chain coordination channels to identify new vulnerabilities as tooling evolves.
What’s Next: The Road to Confidential DAOs
The next phase of DAO evolution will see privacy not as a bolt-on but as a core design principle, especially as cross-chain activity grows. Expect more protocols to follow Mantabridge’s lead in integrating zero-knowledge cryptography at the bridge layer. Regulatory clarity will lag behind technical innovation, so DAOs must stay agile: maintain robust documentation of privacy practices and be ready to adapt as legal frameworks catch up.
The bottom line? MEV protection and cross-chain treasury privacy are now table stakes for any serious decentralized organization operating in 2025’s multi-chain landscape. Those who embrace these advances early will not only protect their assets, they’ll set the standard for secure, resilient governance in an increasingly adversarial environment.