Confidentiality in DAO voting is no longer a theoretical luxury, it’s rapidly becoming a core requirement for healthy decentralized governance. As DAOs mature, the need for private, tamper-resistant voting mechanisms has moved to the forefront of both technical research and practical implementation. Zero-knowledge proofs (ZKPs) have emerged as the linchpin technology enabling DAOs to achieve this powerful combination of privacy and verifiability without sacrificing on-chain transparency.

Why Confidential Voting Matters for DAOs
The public nature of blockchain governance has historically exposed DAOs to several vulnerabilities: voter coercion, bandwagon effects, and even targeted retaliation. When every vote is visible on-chain, participants may feel pressured to vote with the crowd or align with influential whales rather than act honestly. This undermines the very ethos of decentralized decision-making.
Recent studies and case analyses underscore that private voting enables more honest participation, reduces corruption risk, and unlocks the true potential of decentralized organizations. According to pse. dev, private voting “prevents corruption, enables more honest participation, and unlocks the full potential of decentralized governance. ” In other words, confidentiality isn’t just about secrecy, it’s about fostering a healthier democratic process within DAOs.
How Zero-Knowledge Proofs Enable Confidential DAO Voting
Zero-knowledge proofs allow one party (the prover) to prove to another (the verifier) that they possess certain information, such as eligibility or vote choice, without revealing any underlying data. In the context of DAOs, ZKPs empower members to:
- Prove eligibility (e. g. , token ownership or membership)
- Cast votes anonymously, shielding choices from public view
- Ensure single-vote guarantees, preventing double-voting while preserving privacy
- Enable public verification that results are correct without exposing individual votes
This cryptographic approach directly addresses the shortcomings of traditional on-chain voting systems where all actions are fully transparent by default. Instead of relying on trust in delegates or off-chain intermediaries, ZKP-based protocols keep ballots confidential while maintaining provable integrity.
Key Benefits and Use Cases of ZKPs in DAO Voting
-

Private and Secure Voting with NounsDAO’s zk-POPVOTE: NounsDAO has implemented Aztec’s zk-POPVOTE system, leveraging zero-knowledge cryptography to ensure that members can prove eligibility and cast votes confidentially. This prevents vote tracing and protects voter privacy, fostering more honest participation.
-
Confidential Delegation via Kite Protocol: Kite Protocol, developed by researchers including Dan Boneh, enables DAO members to delegate, revoke, and re-delegate voting power without revealing delegate identities, even to the delegates themselves. This enhances privacy and flexibility in governance.
-
Anonymous Ranked-Choice Voting with ElectAnon: ElectAnon is a blockchain-based protocol that uses ZKPs to facilitate anonymous, scalable ranked-choice voting. It ensures both the integrity and verifiability of elections while keeping voter choices confidential.
-

Eligibility Verification and One-Vote Assurance via AnonyVote: AnonyVote allows DAO members to anonymously verify their eligibility and ensures each user can only vote once per poll, all without exposing identities. This upholds fairness and prevents double voting.
-
Enhanced Governance Integrity and Member Trust: By integrating ZKPs, DAOs can mitigate vote coercion, bandwagon effects, and voter intimidation. This leads to more secure, tamper-resistant voting processes and strengthens trust in decentralized governance.
Pioneering Protocols: Real-World Implementations in Focus
The leap from theory to practice is already underway. Several leading protocols have integrated zero-knowledge proof systems into their governance frameworks:
- NounsDAO’s zk-POPVOTE: By adopting Aztec’s zk-POPVOTE framework, NounsDAO enables members to prove their right to vote without exposing their identity or vote content. This system leverages advanced zk-SNARK circuits for efficient proof generation and verification.
- Kite Protocol: Developed by cryptography experts including Dan Boneh, Kite allows for private delegation, members can delegate or revoke voting power without revealing who received it. Even delegates themselves cannot see who delegated votes to them.
- AnonyVote and ElectAnon: These platforms introduce anonymous eligibility verification and ranked-choice voting using ZKPs. Each poll is cryptographically unique, ensuring one-person-one-vote while keeping ballots secret.
- S2DV: This scalable system combines Groth16 zk-SNARKs with ElGamal encryption for robust security and computational efficiency in large-scale DAO elections.
This wave of innovation is rapidly transforming how DAOs approach privacy and security. For a deep dive into implementation strategies and technical architectures behind these systems, see Implementing Zero-Knowledge Proofs for Confidential DAO Voting.
Technical Foundations: Smart Contracts Meet Cryptography
The backbone of confidential DAO voting is an interplay between smart contracts and advanced cryptography:
- Smart Contracts: Enforce correct vote casting and tallying while keeping ballots encrypted.
- ZK-SNARK Circuits: Generate compact proofs that verify voter eligibility and ballot validity without leaking sensitive information.
- User Interfaces: Abstract away cryptographic complexity so members can participate easily via wallets or dApps.
- Key Management: Securely stores credentials necessary for proof generation without risking exposure or loss.
This architecture ensures that no single component sees both who voted and how they voted, a critical property for truly confidential governance.
Yet, implementing zero-knowledge proofs in DAOs is not without its challenges. The complexity of cryptographic protocols can create barriers to adoption, especially for communities with limited technical resources. Smart contract vulnerabilities, inefficient proof generation, and poor user experience are persistent hurdles. However, the rapid evolution of tools and standards is making confidential DAO voting increasingly accessible and robust.
Protocols like Kite and S2DV are setting new benchmarks for scalability and usability. Groth16 zk-SNARKs, for example, offer efficient proof sizes and fast verification times, critical factors for high-participation DAOs. Meanwhile, modular front-end interfaces abstract away the underlying cryptography, enabling members to vote privately with just a few clicks. As these solutions mature, we’re witnessing a shift from experimental pilots to production-grade deployments across leading organizations.
Practical Considerations: What DAO Builders Need to Know
For DAO founders and governance architects considering confidential voting, several best practices have emerged:
Best Practices for Zero-Knowledge Proofs in DAO Voting
-
Adopt Proven ZKP Voting Protocols: Utilize established protocols like zk-POPVOTE (as used by NounsDAO), Kite Protocol, ElectAnon, and AnonyVote to ensure robust privacy and verifiable vote integrity.
-

Integrate ZK-SNARK Circuits for Eligibility and Privacy: Implement ZK-SNARK circuits to allow members to prove eligibility and cast votes without revealing identities or choices, enhancing both privacy and security.
-

Deploy Secure Smart Contracts: Use well-audited smart contracts to manage the voting process, ensuring that votes are recorded and tallied correctly while maintaining confidentiality.
-
Ensure User-Friendly Front-End Interfaces: Provide intuitive interfaces for voters, making it simple to participate in confidential voting while preserving privacy through seamless ZKP integration.
-
Implement Robust Key Management Systems: Securely manage cryptographic keys and credentials to prevent unauthorized access and ensure that only eligible members can generate and verify ZKPs.
-
Enable Anonymous Delegation Mechanisms: Adopt protocols like Kite that allow private delegation, so members can delegate, revoke, or re-delegate voting power without revealing relationships or influencing outcomes.
-
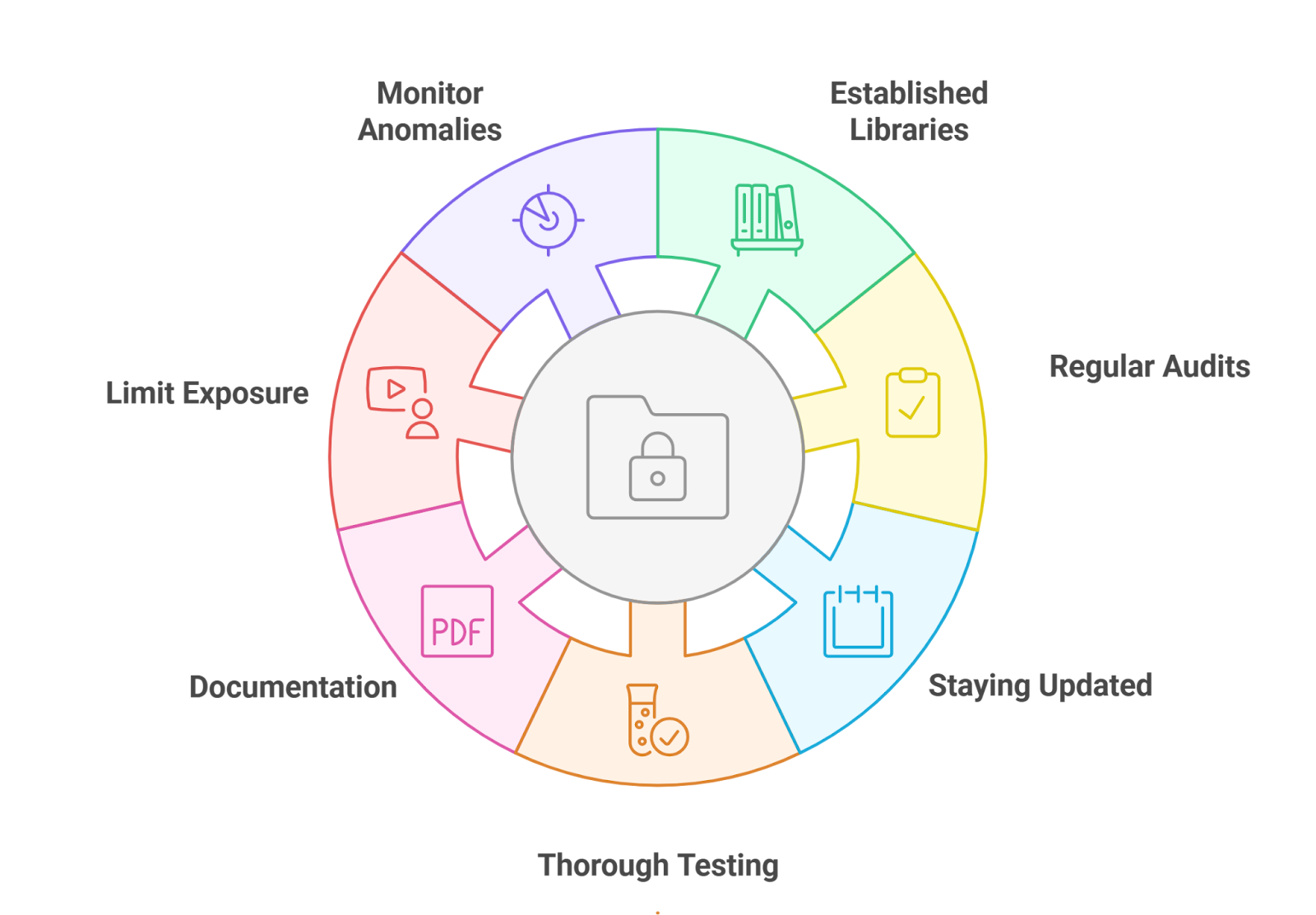
Conduct Independent Security Audits: Regularly audit ZKP implementations and smart contracts to identify vulnerabilities and ensure the system maintains confidentiality and integrity.
Security audits are non-negotiable, ZKP circuits and smart contracts must be rigorously tested before mainnet launch. User education is equally vital; onboarding materials should demystify the privacy guarantees and guide members through the new voting process. Finally, key management strategies must be resilient against loss or compromise without introducing centralized points of failure.
The trend is clear: as more DAOs adopt private governance frameworks, privacy-preserving voting will become a baseline expectation rather than a niche feature. This movement is already influencing protocol design across Ethereum L2s and alternative chains.
The Future of Confidential DAO Voting
The next generation of confidential DAO voting systems will likely integrate even more advanced cryptographic primitives, think recursive SNARKs or threshold cryptography, to further enhance scalability and trustlessness. Interoperability between privacy layers will allow DAOs to coordinate across chains without leaking sensitive data.
Ultimately, zero-knowledge proofs are empowering DAOs to reclaim genuine democratic participation while maintaining verifiable integrity on public ledgers. As adoption accelerates, expect confidential voting to become as foundational as token-gated access or on-chain treasuries in decentralized governance toolkits.
If you want to explore technical blueprints or step-by-step guides for integrating ZKPs into your own organization’s governance stack, see How to Implement Zero-Knowledge Proofs for Confidential DAO Voting.