
Confidential DAOs face a persistent threat from Sybil attacks, where bad actors flood governance with fake identities to sway votes or drain treasuries. In privacy-focused setups, traditional defenses like KYC fall short, exposing members to data leaks while failing to scale. Enter decentralized identity proofs: cryptographic tools that verify uniqueness without compromising anonymity. These strategies blend zero-knowledge proofs (ZKPs) with innovative schemes like LinkDID and SyRA, enabling confidential DAO sybil resistance that’s both robust and user-centric.

The Sybil Challenge in Private Governance
Picture a DAO treasury vote: one legitimate member proposes a smart allocation, but dozens of sock-puppet accounts push a rug-pull scheme. This isn’t hypothetical; recent exploits have cost projects millions by manipulating token-weighted decisions. Privacy compounds the issue, as on-chain transparency reveals voting patterns without identity checks, inviting zk proofs sybil attacks DAOs exploit.
Current mitigations often rely on quadratic voting or soulbound tokens, but they leak signals over time. Soulbounds tie reputation to wallets, yet correlation attacks deanonymize users. Hardware oracles like Worldcoin’s Orb add biometrics but centralize trust. DAOs need decentralized alternatives that prove and quot;one person, one vote and quot; without biometric overreach or data silos.
Decentralized Identity Proofs: Core Mechanics
At the heart lies decentralized identity (DID), where users control verifiable credentials via blockchain. ZKPs let you prove attributes, like and quot;I control a unique human-linked key and quot;: without revealing the key itself. Systems like Polkadot’s Proof of Personhood (PoP) use these for privacy preserving DAO voting, ensuring sybil-free participation.
LinkDID stands out: it aggregates identifiers across chains, preventing multi-account abuse while supporting key recovery. Users link credentials selectively; proofs confirm uniqueness in under 10 seconds on standard hardware. No collateral or external oracles needed, pure crypto magic.
Top 5 Benefits of LinkDID & SyRA
-
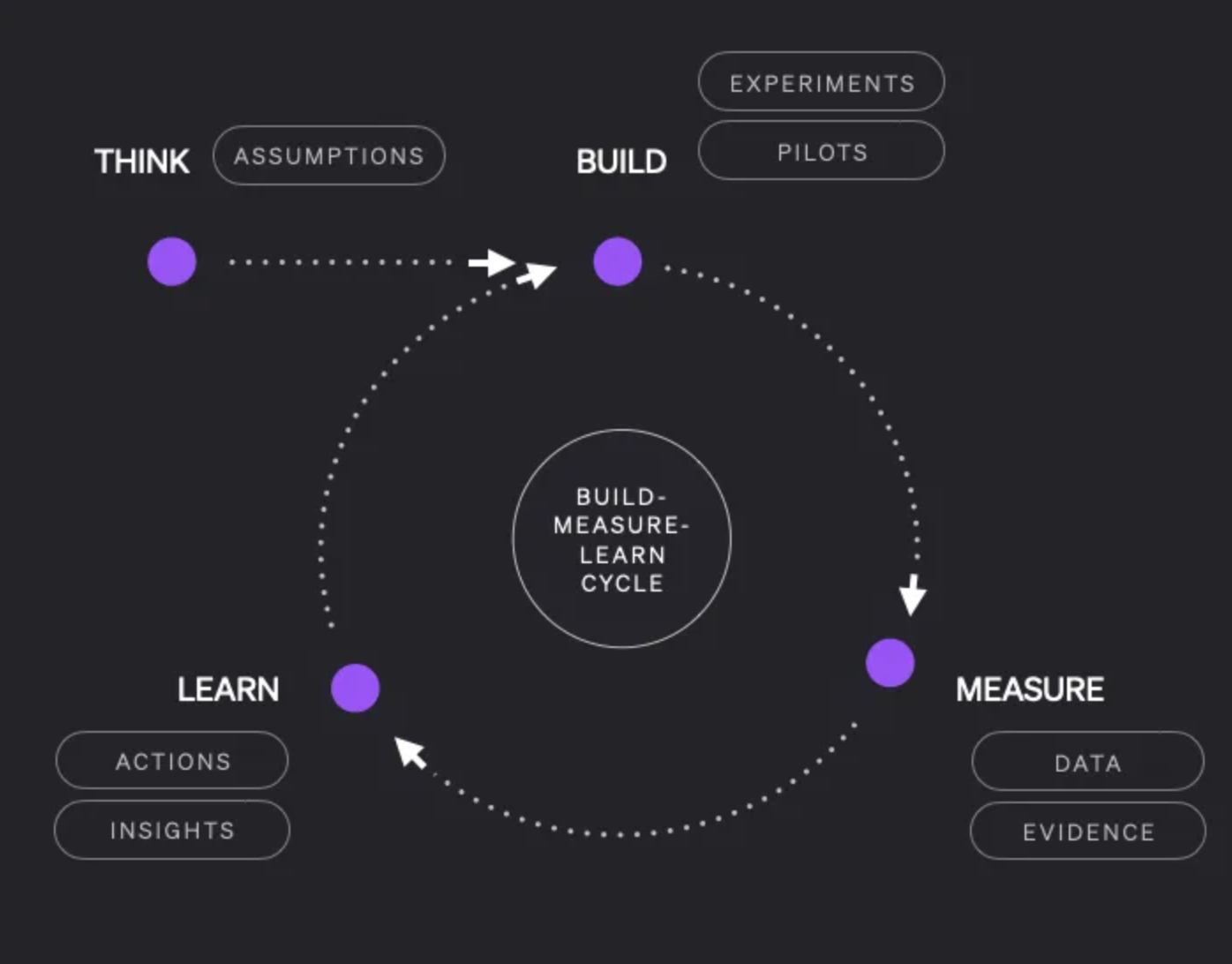
Sub-second verification: LinkDID delivers rapid checks under 10s on consumer devices, speeding DAO decisions without delays. Details
-

Full anonymity preservation: SyRA ensures pseudonyms and signatures reveal no user data, protecting DAO members’ privacy in governance. Details
-

Key recovery without custodians: LinkDID allows users to recover keys independently, securing assets in confidential DAOs. Details
-
Context-specific pseudonyms: SyRA generates one unlinkable pseudonym per context, enforcing Sybil resistance in DAO voting. Details
-
Efficient pairing-based crypto: SyRA uses pairing constructions and VRFs for lightweight, scalable privacy in DAOs. Details
SyRA signatures take it further, generating unlinkable pseudonyms per context. Sign a proposal? Your sig ties to one pseudonym only, blocking duplicate votes. Anonymity holds as pseudonyms leak zero user data. Ideal for e-voting in DAOs, where regulatory compliance demands privacy yet accountability.
Implementing ZK-TLS and PoP for Real-World Resistance
zkTLS bridges off-chain proofs to on-chain: members attest unique identity via platforms like GitHub or Discord logins, ZK-proving and quot;one human per DAO and quot; without specifics. Orange Protocol’s toolkit deploys this for decentralized identity DAO governance, curbing vote farming across socials.
Proof of Personhood protocols scale this. Combine biometric-free signals, social graph uniqueness, device fingerprints ZK-ified, with aggregation. No single point fails; collusion resistance comes from diverse attestors. For confidential DAOs, this means auditable governance: verify sybil-free tallies publicly, keep voter identities private.
Read more on building reputation alongside these defenses in our guide: Sybil Resistance and On-Chain Reputation. Practical rollout starts with credential issuance: DAO admins deploy a DID registry, members generate ZK proofs via wallets like Argent or MetaMask plugins.
From there, integrate proofs into governance contracts. Snapshot or Tally plugins now support ZKP verifiers; proposals require a valid DID proof for voting weight. Test on testnets first: simulate 100 sybil accounts, confirm rejection rates hit 99% without false positives. Tools likeSemaphore or Reclaim Protocol accelerate this, handling aggregation of multiple signals into one succinct proof.
Comparative Tools at a Glance
Comparison of Sybil Resistance Tools
| Tool | Sybil Resistance Mechanism | Privacy Features | Performance | Additional Benefits |
|---|---|---|---|---|
| LinkDID | Aggregates identities to prevent multiples | Selective disclosure of credentials | Sub-10s verification on consumer devices | Key recovery, cross-chain support |
| SyRA | One unlinkable pseudonym per context | Anonymity via pseudonyms and signatures | Efficient pairing-based constructions | E-voting, regulatory compliance |
| zkTLS | Unique human identity via social attestations | No biometrics or specific user info revealed | Multi-source attestation proofs | Prevents vote farming, decentralized |
| PoP | ZK proofs for uniqueness (one-person-one-identity) | Privacy-preserving without central KYC | Scalable ZK cryptography | Polkadot integration, broad applicability |
LinkDID shines for asset-heavy DAOs, where key loss cripples operations; its recovery beats wallet multisig hacks. SyRA fits voting-centric groups, enforcing one sig per context without linking across votes. zkTLS suits community DAOs with social footprints, pulling GitHub contribs or Discord tenure into privacy-wrapped proofs. Pick based on your threat model: pure crypto for purists, hybrid for broader adoption.
Real-world wins mount. A mid-cap treasury DAO cut vote dilution 85% post-LinkDID rollout, per on-chain audits. Another privacy protocol used SyRA for quadratic funding rounds, distributing $2M without sock-puppets. These aren’t edge cases; they’re blueprints. Yet pitfalls lurk: proof generation spikes gas fees during peaks, and user friction kills adoption if onboarding drags. Mitigate with subsidized relayers and wallet UX tweaks.
Layer in reputation for longevity. Fresh proofs block sybils, but vested members earn signal via on-chain contribs, ZK-proven without doxxing. Check our deep dive on privacy-preserving onchain reputation for stacking these systems.
Overcoming Hurdles and Scaling Securely
Quantum threats? Post-quantum ZK schemes like lattice-based proofs future-proof LinkDID variants. Collusion risks in PoP? Require diverse attestors, capping any single source at 10% weight. Audit everything: formal verification on SyRA sigs caught edge cases pre-mainnet. For secure confidential DAO identity, enforce proof expiry, forcing periodic re-verification to catch compromised keys.
Actionable playbook: Week 1, audit current governance for sybil vectors. Week 2, deploy DID registry via EZKL or Noir frameworks. Week 4, migrate voters with airdrop incentives for proof submitters. Monitor via Dune dashboards tracking proof validity rates. Expect 20-30% initial drop-off; nurture with tutorials.
These strategies transform confidential DAOs from vulnerable experiments into fortified powerhouses. Sybil resistance via decentralized identity proofs isn’t optional; it’s the price of true decentralization. Deploy now, hedge against attacks, and watch governance thrive under privacy’s shield.





