As DAOs (Decentralized Autonomous Organizations) mature, privacy and confidentiality are becoming non-negotiable features for governance, treasury management, and member participation. The open nature of blockchains is at odds with the need for confidential voting, private proposals, and secure financial operations. To address these challenges, two advanced technologies have emerged as foundational pillars: Homomorphic Encryption (HE) and Trusted Execution Environments (TEEs). Each brings unique strengths to confidential DAO architecture, but also introduces distinct trade-offs in terms of performance, security assumptions, and operational complexity.
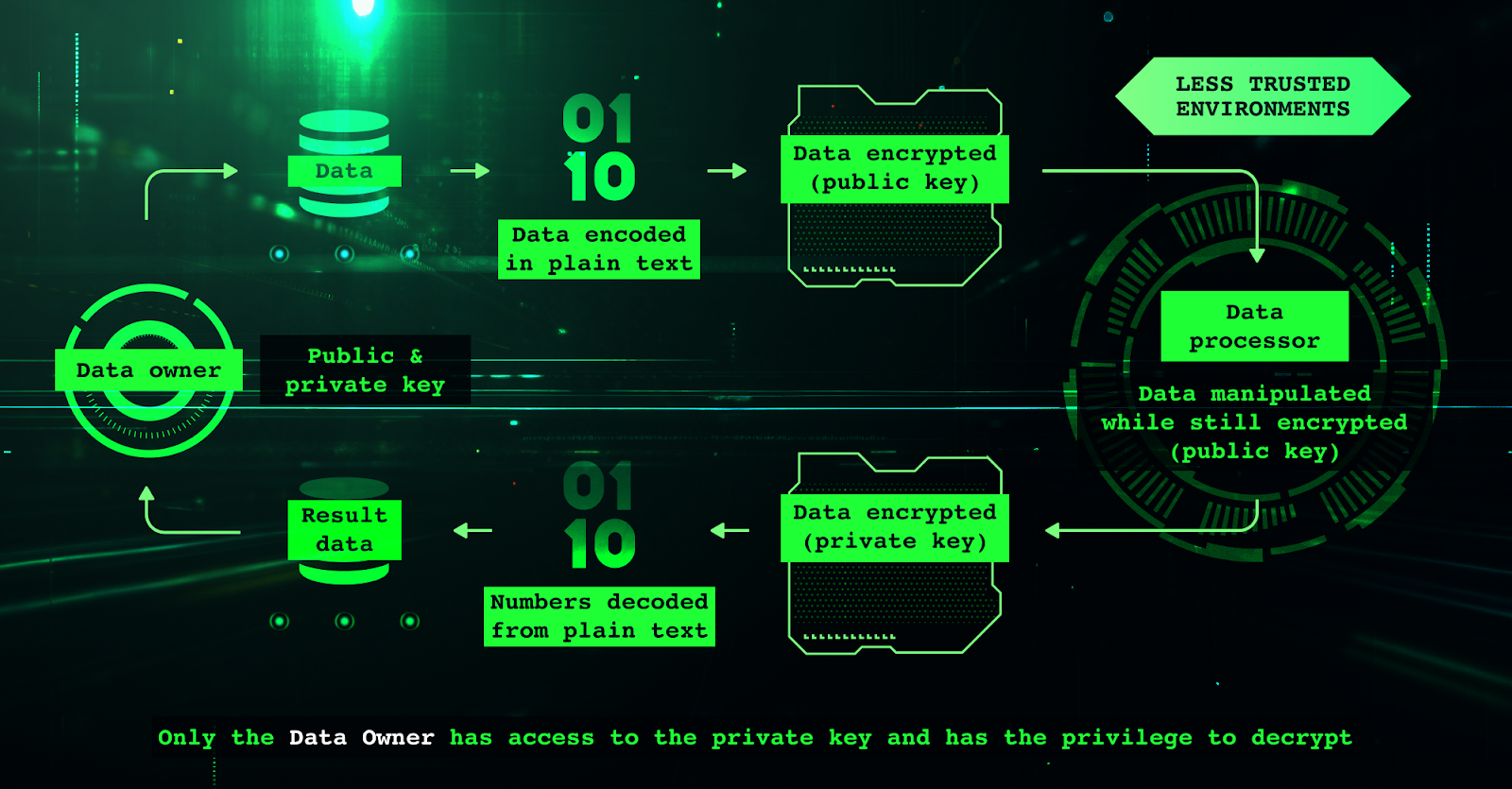
Homomorphic Encryption: Privacy Without Compromise
At the heart of homomorphic encryption DAO design is the ability to perform computations on encrypted data without ever exposing its contents. This cryptographic breakthrough allows DAOs to execute functions such as vote tallying or proposal scoring while safeguarding the privacy of each participant’s input. For example, a member can submit an encrypted vote or token allocation; the system computes aggregate results directly on ciphertexts, never revealing individual choices.
This approach is gaining traction with projects like Fhenix, which leverages Fully Homomorphic Encryption (FHE) for confidential governance workflows. With FHE, DAOs can enable:
- Private voting mechanisms: Votes remain secret even during processing.
- Confidential proposal evaluation: Sensitive data used in proposals is never decrypted by validators or smart contracts.
- Discreet treasury allocations: Financial operations can be computed securely without exposing underlying figures.
The appeal is clear: cryptographic guarantees that are independent of hardware trust assumptions. However, the computational cost remains significant. Even with recent advances in FHE libraries and specialized hardware acceleration, performance overheads can be prohibitive for real-time or high-frequency DAO operations. This is a critical consideration when designing confidential DAO architecture for speed-sensitive applications.
Trusted Execution Environments: Hardware-Backed Confidentiality
Trusted Execution Environments blockchain solutions offer a different path to private smart contracts. TEEs are isolated hardware enclaves within processors that execute code securely, shielded from the host operating system and even cloud providers. In practice, this means sensitive computations like vote tallying or financial reconciliations can run inside these enclaves without leaking data to external observers.
The Oasis Network exemplifies this model by running smart contracts inside TEEs to deliver confidential voting for DAOs (Oasis Network blog). This approach provides:
- Low-latency processing: Near real-time computation suitable for dynamic governance events.
- Simplified developer experience: Existing codebases often require fewer modifications compared to HE-based systems.
- Hardware-enforced isolation: Reduces attack surfaces compared to traditional software-only approaches.
The principal trade-off? TEEs introduce a dependency on hardware manufacturers’ security assurances and supply chain integrity. While attacks against enclaves are rare and technically demanding, they are not impossible, a risk that must be weighed carefully when building confidential DAO infrastructure at scale.
Key Differences: Homomorphic Encryption vs. TEEs in DAOs
-
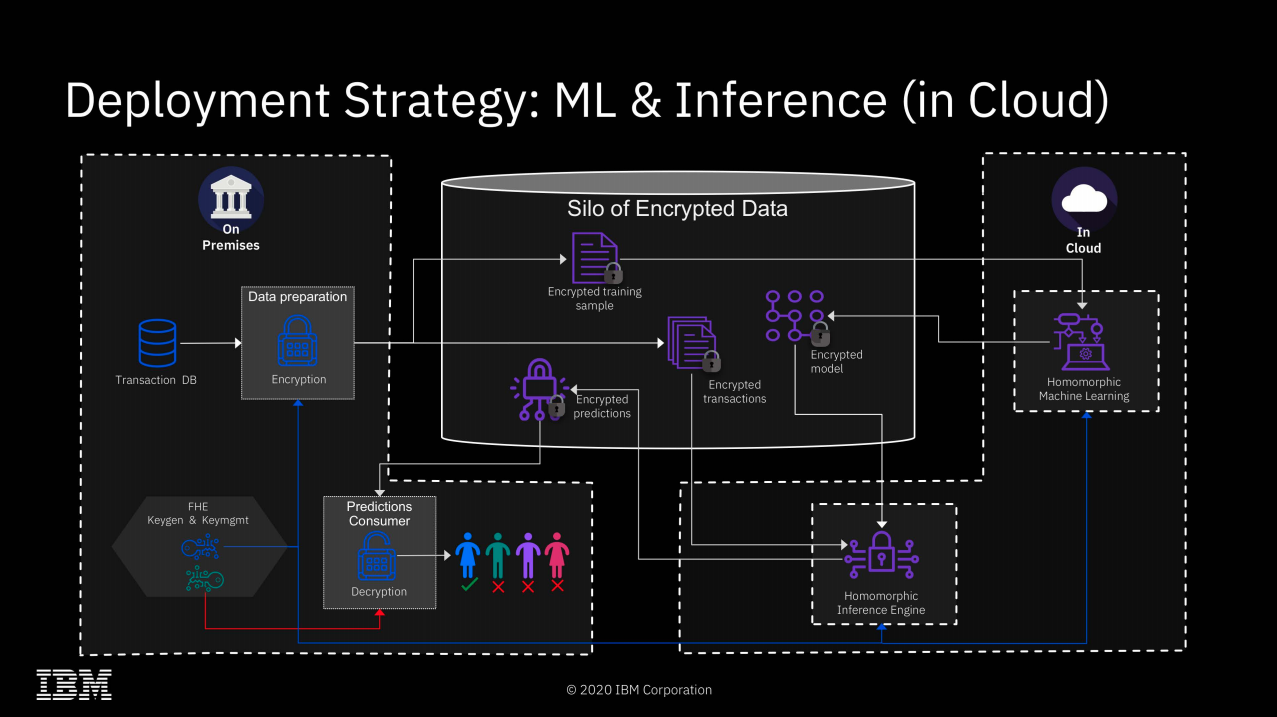
Computation on Encrypted Data: Homomorphic Encryption (HE) enables computations directly on encrypted data without decryption, preserving privacy throughout the process. In contrast, Trusted Execution Environments (TEEs) require data to be decrypted within a secure enclave for processing.
-
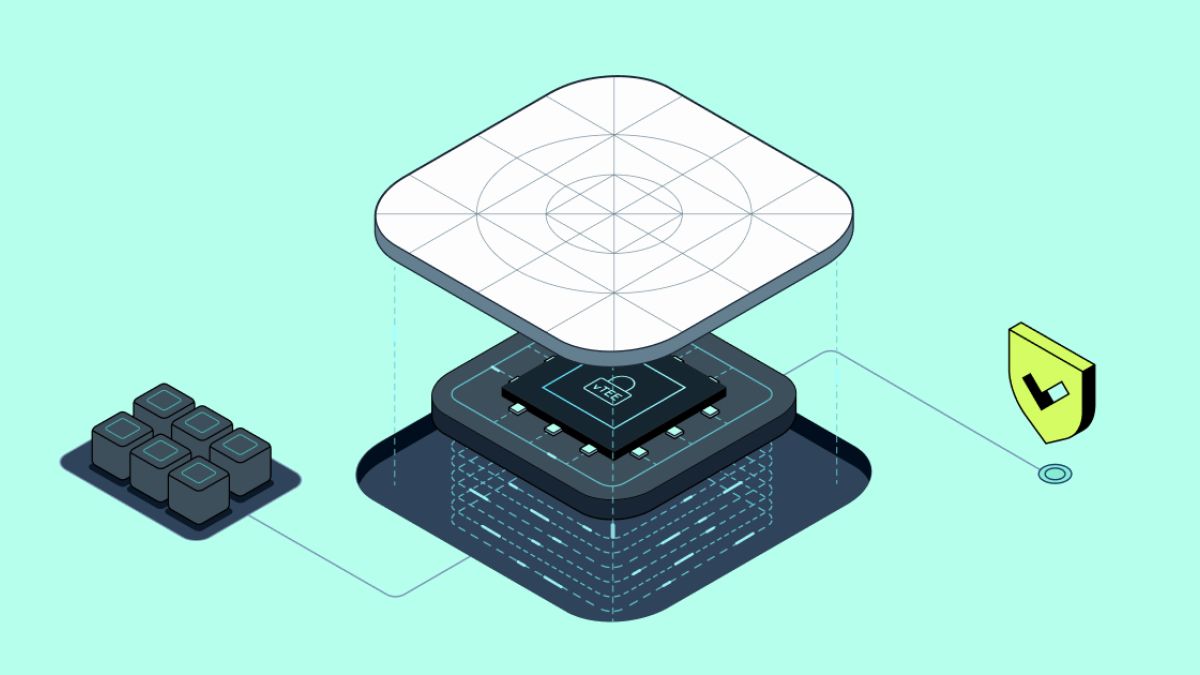
Performance and Efficiency: TEEs generally offer higher performance and lower latency for confidential computations, as they leverage hardware-based isolation. HE, while highly secure, is computationally intensive and can introduce significant performance overhead, especially for complex operations.
-
Security Model: HE provides strong cryptographic guarantees without relying on hardware trust, minimizing exposure to hardware vulnerabilities. TEEs depend on the security of the underlying hardware and its supply chain, introducing a trust dependency on hardware manufacturers.
-

Implementation in DAOs: Projects like Fhenix use Fully Homomorphic Encryption to enable confidential voting and proposal evaluations in DAOs. Conversely, Oasis Network leverages TEEs for secure and private DAO voting via smart contracts executed in isolated environments.
-
Hybrid Approaches: Solutions like CHEX-MIX combine HE and TEEs to balance privacy and performance, allowing DAOs to perform secure computations efficiently while maintaining robust confidentiality.
Pioneering Hybrid Architectures: Combining Strengths for Next-Gen Confidential DAOs
The market has responded with innovative hybrid models that blend HE’s cryptographic rigor with TEE’s performance advantages. Microsoft’s CHEX-MIX framework demonstrates how combining these paradigms enables privacy-preserving machine learning across untrusted cloud infrastructure (CHEX-MIX publication). In such systems:
- Sensitive inputs are encrypted via FHE before being sent to the cloud.
- The TEE processes encrypted data efficiently while maintaining isolation from untrusted components.
- The result is decrypted only by authorized parties with appropriate keys, never by the infrastructure provider itself.
This fusion not only enhances security but also paves the way for scalable private smart contracts in high-stakes DAO environments where both speed and confidentiality matter deeply.
As these architectures evolve, DAOs are faced with a nuanced set of choices. The push for confidential DAO architecture is not simply about selecting the most secure technology, but rather about orchestrating a balance between cryptographic purity, hardware trust, operational efficiency, and community transparency. Each DAO must assess its unique threat model and governance needs before settling on an implementation path.
Operational Considerations: Building for Privacy and Performance
Implementing homomorphic encryption or TEEs within a DAO ecosystem requires careful planning. For DAOs focused on privacy-centric governance, such as whistleblower protection, sensitive treasury allocations, or confidential voting, the computational overhead of HE may be justified by its unrivaled cryptographic assurances. On the other hand, DAOs that prioritize speed and seamless user experience may lean toward TEE-backed solutions, accepting some degree of hardware trust in exchange for lower latency and higher throughput.
Hybrid models are gaining traction precisely because they allow DAOs to fine-tune the privacy-performance trade-off. By encrypting only the most sensitive operations with FHE and executing the rest within TEEs, organizations can achieve robust confidentiality without sacrificing operational agility. This layered approach is particularly relevant as regulatory scrutiny increases and DAOs seek to protect both member privacy and organizational integrity.
Practical Steps: Deploying Confidential DAO Infrastructure
For teams building next-generation confidential DAOs, several best practices are emerging:
Best Practices for Deploying Confidential DAO Infrastructure
-

Leverage Homomorphic Encryption for Private Voting: Implement Fhenix or similar platforms to enable confidential voting and proposal evaluation. Homomorphic encryption ensures computations are performed on encrypted data, preserving member privacy throughout the process.
-

Utilize Trusted Execution Environments for Secure Smart Contracts: Deploy smart contracts within Oasis Network or other TEE-enabled blockchains to protect sensitive operations such as vote tallying and financial transactions in isolated, hardware-secured environments.
-

Adopt Hybrid Approaches for Enhanced Security and Performance: Combine homomorphic encryption with TEEs using frameworks like CHEX-MIX to balance robust privacy with computational efficiency, especially for complex, privacy-preserving computations.
-
Assess Security vs. Performance Trade-offs: Carefully evaluate the performance overhead of homomorphic encryption against the hardware trust dependencies of TEEs. Choose the architecture that aligns with your DAO’s confidentiality and efficiency requirements.
-
Regularly Audit and Update Confidential Infrastructure: Conduct ongoing security audits and keep cryptographic libraries, TEE firmware, and smart contract code up to date to mitigate emerging threats and vulnerabilities.
- Threat modeling: Map out adversaries, both external hackers and internal actors, and identify which data flows require maximum confidentiality.
- Key management: In HE-based systems, securely managing encryption keys is paramount; in TEE-based systems, attestation protocols must be rigorously enforced.
- Auditing: Regularly audit both cryptographic codebases (for HE) and hardware supply chains (for TEEs) to maintain trust assumptions over time.
- User education: Ensure DAO members understand how their privacy is protected, and what residual risks remain, so they can participate with confidence.
The open-source community continues to drive innovation at this intersection. Frameworks like Fhenix, Oasis Network’s confidential contracts (Oasis blog), and Microsoft’s CHEX-MIX (CHEX-MIX publication) offer real-world blueprints for teams seeking to implement privacy-first governance at scale.
The Road Ahead: Confidentiality as a Competitive Advantage
The competitive landscape for DAOs is shifting: those who invest in advanced confidentiality measures will earn the trust of users navigating an increasingly regulated digital economy. As performance bottlenecks in FHE are reduced through research breakthroughs, and as TEE security hardens against emerging threats, the toolkit for building truly private smart contracts will only expand.
The future of decentralized governance depends on our ability to blend transparency with selective secrecy. By leveraging homomorphic encryption, trusted execution environments, or hybrid architectures tailored to specific use cases, DAOs can achieve this delicate balance, enabling innovation without sacrificing privacy or security.