Trust is the bedrock of any thriving DAO, but in the age of on-chain transparency, confidentiality has become just as crucial. As DAOs scale and mature, members are demanding more than just open ledgers and public votes – they want privacy tools that enable secure, honest participation without sacrificing decentralization. The latest wave of confidential governance solutions is answering this call, transforming how DAOs operate and how members engage.
Why DAOs Need Confidential Governance Now
Decentralized Autonomous Organizations were born from a vision of radical transparency. Yet, as the ecosystem grows, the pitfalls of full transparency are hard to ignore: vote buying, coercion, whale dominance, and the chilling effect of public scrutiny. Open voting records can expose members to undue influence, retaliation, or even legal risks. This is why the push for confidential governance in DAOs is gaining momentum across the blockchain industry.
Recent research and real-world DAO experiments underscore the urgency:
Top Reasons DAOs Are Embracing Confidential Governance
-

Prevents Bribery and Vote Buying: Confidential governance solutions like Shutter Network and Aztec Network shield individual votes from public view, making it nearly impossible for malicious actors to verify if someone voted a certain way—dramatically reducing the risk of bribery and collusion.
-

Protects Minority Voters from Retaliation: By leveraging privacy technologies such as Oasis Protocol and Zama, DAOs ensure that minority voices can participate without fear of backlash or social pressure, fostering a more inclusive and balanced governance structure.
-

Enables More Honest Participation: Solutions like PSE’s privacy voting tools and COTI empower members to vote according to their true preferences, free from peer pressure or external scrutiny, which leads to more genuine and effective decision-making.
-

Secures Delegated Voting Power: Platforms such as Kite enable private delegation, allowing members to assign or revoke voting power without exposing their choices, thus preventing undue influence and maintaining trust in the delegation process.
-

Restores Confidence in DAO Governance: As highlighted by Decent DAO and DoraHacks, implementing confidential voting mechanisms helps rebuild trust among participants, especially as public voting has led to declining confidence due to manipulation and lack of privacy.
As outlined by Oasis Protocol, NounsDAO, and Zama, private DAO voting solutions are rapidly maturing, offering practical paths to shield both identities and decisions without compromising verifiability. The result? A more level playing field and a culture of trust that encourages broader participation.
Core Technologies Driving Private DAO Voting Solutions
The foundation of confidential DAO proposals and voting is cryptography – but not the kind that simply locks away data. Instead, cutting-edge techniques like Zero-Knowledge Proofs (ZKPs), Trusted Execution Environments (TEEs), and homomorphic encryption let DAOs achieve the best of both worlds: privacy with provable correctness.
Zero-Knowledge Proofs (ZKPs): These allow members to prove eligibility or cast a vote without revealing any underlying details. Solutions like MACI use zkSNARKs to make voting anonymous and tamper-proof, while still allowing the DAO to verify the vote tally. This means members can participate without fear of doxxing or social pressure.
Trusted Execution Environments (TEEs): TEEs are secure enclaves within processors – think of them as vaults for code execution. The Oasis Network leverages TEEs to keep DAO votes confidential while ensuring the results are accurate and auditable. This approach is especially valuable for DAOs handling sensitive proposals or high-value treasury decisions.
Homomorphic Encryption: This advanced method lets computations happen on encrypted data. Zama’s confidential DAO voting, for example, keeps both token balances and individual votes secret throughout the process. Only the final outcome is revealed, not how each member voted or how much voting power they wielded.
Practical Steps to Implement Confidential Governance
So how can a DAO actually move from theory to practice? While the cryptography can be complex, the roadmap for integrating privacy tools into decentralized governance is becoming clearer:
Actionable Steps for Confidential DAO Governance
-

Define Clear Privacy Goals: Identify which governance elements—such as voting, member identities, or treasury management—require confidentiality. Setting these priorities ensures your DAO adopts the right privacy measures from the start.
-

Select the Right Privacy Technology: Choose proven solutions like Zero-Knowledge Proofs (ZKPs)—used by MACI and Aztec Network—for anonymous voting, or Trusted Execution Environments (TEEs) as implemented by Oasis Network for confidential vote processing.
-

Develop and Integrate Secure Protocols: Build or adopt open-source, audited protocols like MACI for ZKP-enabled voting, or leverage TEE-based frameworks from Oasis Protocol to ensure votes and sensitive actions remain confidential.
-
Conduct Regular Security Audits: Partner with established blockchain security firms (such as Trail of Bits or ConsenSys Diligence) to audit your confidential governance mechanisms, identifying and patching vulnerabilities before they can be exploited.
-
Educate and Empower DAO Members: Provide clear, accessible resources and workshops on privacy tools and confidential governance practices. Use platforms like Oasis Learn or Ethereum.org to help members understand how their privacy is protected and why it matters.
Protocols like Kite are now enabling private delegation, letting members assign voting power without revealing their choices – even to the delegate themselves. This not only prevents vote buying but also preserves the autonomy of every participant.
For a deeper dive into how encrypted voting, private proposals, and operational security can empower your DAO, check out this detailed guide.
Confidential governance is not just a technical upgrade – it’s a cultural shift for DAOs. When members know their votes and identities are shielded, they’re far more likely to speak their minds, propose bold ideas, and challenge entrenched interests. This unleashes the true potential of decentralized governance: a system where every voice counts, not just those with the loudest wallets.
“Privacy is the precondition for honest governance. Without it, DAOs risk devolving into plutocracies or echo chambers. ”
Recent deployments by DAOs such as NounsDAO and integrations with privacy-focused networks like Oasis and COTI are proving that confidential governance is not only possible but practical at scale. These projects are leveraging a mix of ZKPs, TEEs, and innovative delegation protocols to ensure that every proposal, vote, and treasury move can be executed without exposing sensitive details to the world.
Building Trust Through Verifiable Privacy
The skepticism that often greets privacy upgrades in DAOs is understandable. How can you be sure votes aren’t tampered with if you can’t see them? This is where the magic of verifiable privacy comes in. Modern privacy tools for DAOs don’t just hide information – they provide cryptographic proofs that everything was done correctly, without leaking any confidential data. Auditors can verify the outcome, members remain protected, and the DAO as a whole becomes more resilient to manipulation.
Here’s a quick snapshot of the privacy toolkit revolutionizing DAOs:
Top Privacy Tools Powering Confidential DAO Governance
-
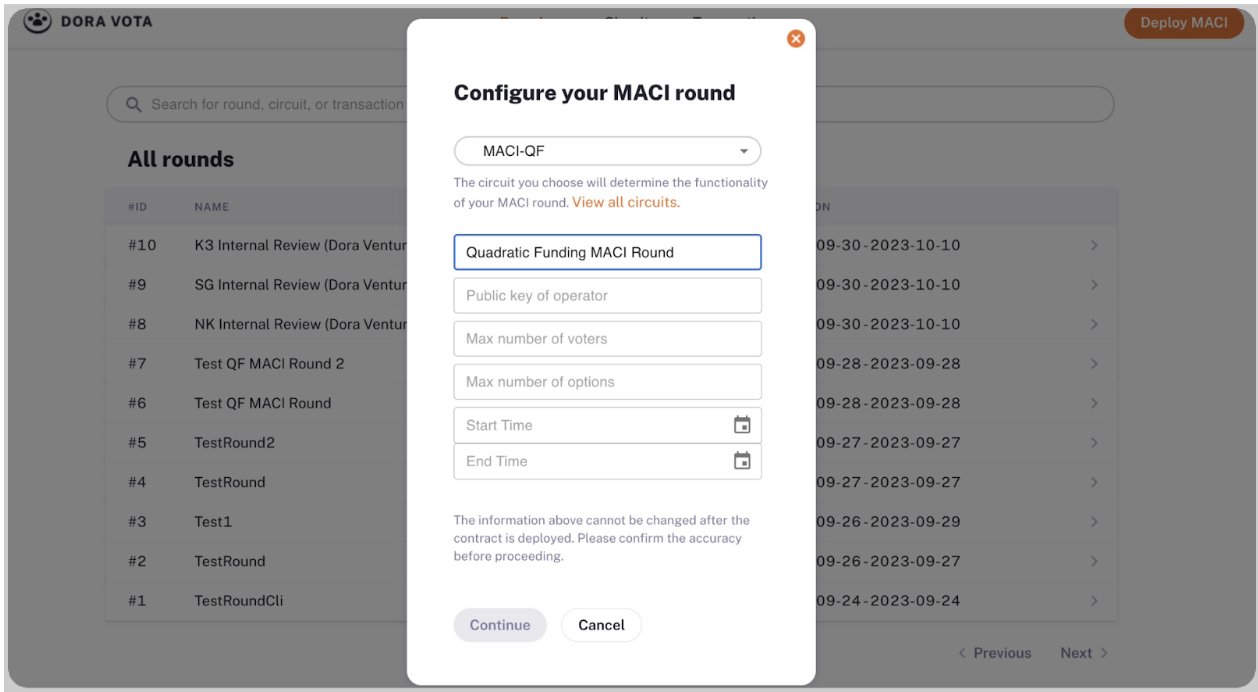
Zero-Knowledge Proofs (ZKPs): zkSNARKs & MACI — ZKPs like zkSNARKs enable DAOs to verify member eligibility and conduct anonymous voting without revealing sensitive data. MACI (Minimum Anti-Collusion Infrastructure) is widely used to ensure tamper-resistant, private voting in DAO governance.
-

Trusted Execution Environments (TEEs): Oasis Network — Oasis Network leverages TEEs to provide shielded smart contract execution and confidential DAO voting, ensuring that votes and sensitive operations remain private and secure from external threats.
-

Homomorphic Encryption: Zama — Zama offers homomorphic encryption solutions that allow DAOs to perform computations on encrypted data. This keeps individual votes and token holdings confidential while still enabling accurate tallying and governance.
-
Private Delegation Protocols: Kite — Kite introduces private delegation for DAO voting, enabling members to delegate, revoke, or re-delegate their voting power without exposing delegate identities, thus preserving participant confidentiality and reducing undue influence.
By combining these tools, DAOs can finally break free from the trade-off between transparency and security. You get auditable, accountable governance – but without putting your members at risk or undermining the integrity of the process.
What Comes Next for Secure Decentralized Governance?
The next frontier is composability: integrating confidential governance modules into DAO frameworks, treasury management, and even off-chain coordination tools. Expect to see more plug-and-play privacy solutions, easier user onboarding, and cross-chain compatibility as the space matures. Community education will be key – after all, privacy only works if members trust and understand the system.
Ultimately, the DAOs that thrive will be those that treat privacy not as an afterthought, but as a core pillar of their social contract. Confidential governance is already restoring trust where it had begun to erode. As these solutions become standard, expect a new wave of innovation – and a far more diverse set of voices shaping the future of decentralized organizations.