Confidential voting is a critical requirement for secure and resilient DAO governance. Traditional on-chain voting exposes every ballot to the public, undermining privacy and opening the door to coercion, bribery, or targeted retaliation. As DAOs scale in size and influence, the demand for robust privacy-preserving voting mechanisms intensifies.
Why Fully Homomorphic Encryption Is a Game-Changer for Private DAO Governance
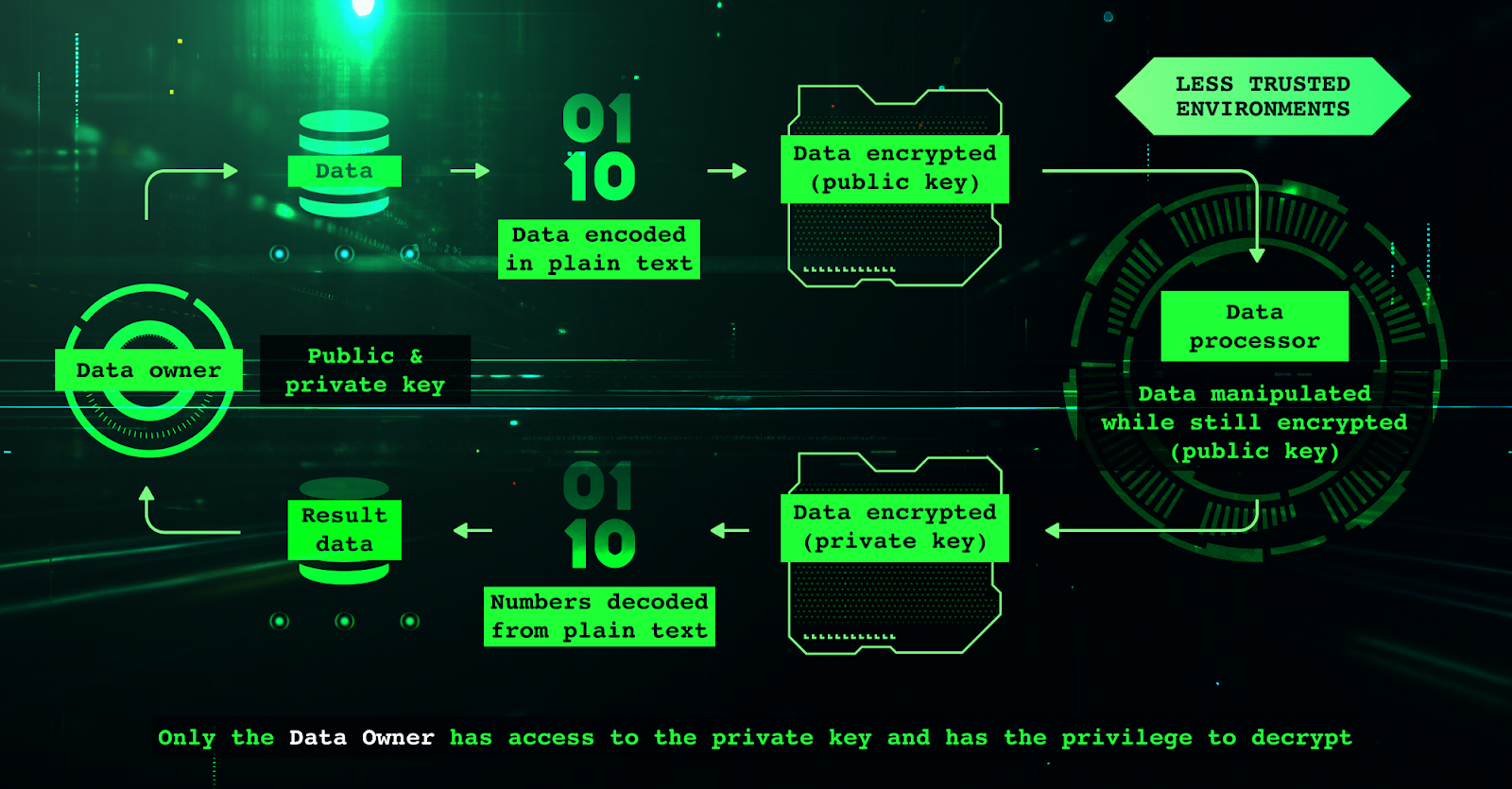
Fully Homomorphic Encryption (FHE) is rapidly emerging as the leading cryptographic solution for confidential voting in DAOs. FHE enables computations directly on encrypted data, so votes can be tallied without ever exposing their contents. This is fundamentally different from traditional encryption schemes that require decryption before processing – a critical vulnerability in adversarial environments.
With FHE, each voter encrypts their ballot before submitting it to the DAO’s smart contract. The contract can then aggregate or count these encrypted votes using FHE-compatible algorithms, producing an encrypted result that only an authorized party (or threshold of parties) can decrypt at the end of the process. At no point are individual votes revealed on-chain or to any third party.

This approach directly addresses major attack vectors such as frontrunning bots, vote buying, and social engineering. By keeping every vote secret until final decryption, DAOs can foster more honest participation and resist manipulation.
Current Market Context: Real-World Projects Pioneering FHE Blockchain Voting
The integration of FHE into DAO tooling has accelerated over the past year. Several projects have launched practical frameworks and developer tools for confidential governance:
Top Open-Source FHE Projects for Confidential DAO Voting
-
Zama’s fhEVM: An open-source extension of the Ethereum Virtual Machine, fhEVM enables smart contracts to process encrypted data using fully homomorphic encryption, making confidential DAO voting on Ethereum possible.
-
AGYSO ZK-DAO-VOTE: This project combines homomorphic encryption and zero-knowledge proofs to deliver privacy-preserving, verifiable DAO voting. The open-source protocol ensures both confidentiality and auditability of votes.
-

Fhenix Encrypted Computation: Fhenix provides open-source tools to integrate encrypted computation into DAOs, supporting private voting and confidential proposals with FHE as the core technology.
- Zama’s fhEVM: An Ethereum Virtual Machine extension supporting FHE operations natively in smart contracts. Zama’s tutorial demonstrates step-by-step how to implement private DAO votes with fhEVM.
- AGYSO ZK-DAO-VOTE: Combines homomorphic encryption with zero-knowledge proofs for both confidentiality and verifiability of votes (source).
- Fhenix Encrypted Computation: Delivers private voting modules designed for regulatory compliance and seamless integration into existing DAOs (details).
The rapid prototyping by teams like Zama and Fhenix signals that confidential governance is no longer theoretical – it’s operationally viable today for DAOs prioritizing privacy.
The Cryptographic Mechanics: How FHE Secures On-Chain Voting
The core innovation behind fully homomorphic encryption DAO voting is its ability to perform mathematical operations (such as addition or multiplication) on ciphertexts. For example, if Alice casts an encrypted “yes” vote (E(1)) and Bob casts an encrypted “no” vote (E(0)), a smart contract can sum these values directly while they remain encrypted:
- E(1) and E(0) = E(1)
The result E(1) reveals only the tally after authorized decryption – never exposing individual preferences during computation or storage. This prevents any observer from linking ballots to voters or inferring interim results mid-vote.
This cryptographic guarantee is why major protocols such as Oasis Protocol have identified FHE as foundational for privacy-preserving e-voting (see analysis here). It also aligns with regulatory requirements around data protection and anti-coercion standards increasingly demanded by institutional participants.
Despite its transformative promise, deploying FHE blockchain voting at scale still presents technical hurdles. Chief among these are computational overhead and latency. FHE operations are inherently more resource-intensive than standard cryptography, which can challenge on-chain scalability and user experience if not engineered carefully. Projects like Zama’s fhEVM are actively optimizing these bottlenecks with custom circuits and hardware acceleration, but DAO architects should benchmark performance early in pilot deployments.
Actionable Steps for DAOs Seeking Confidential Voting
For DAOs aiming to operationalize private DAO governance using FHE, a phased integration approach is recommended:
- Pilot with Small Proposals: Start by running testnet or off-chain votes on low-risk topics to validate the cryptographic workflow and UX.
- Select Proven Frameworks: Choose mature libraries like Zama’s fhEVM or Fhenix modules for initial implementation (Zama tutorial). Avoid unvetted cryptographic code in production.
- Design for Auditability: Pair FHE with zero-knowledge proofs to enable public verification of tally correctness without exposing individual votes (AGYSO example).
- Plan Decryption Governance: Implement threshold decryption so no single party can reveal results unilaterally. Use multi-sig or distributed key ceremonies as needed.
- User Education and Wallet Integration: Provide clear instructions and wallet plugins so participants understand the privacy guarantees and how to cast encrypted ballots safely.
Key Benefits: Why Confidential Voting Matters Now
The shift toward confidential voting in DAOs, powered by FHE, is not just about privacy for its own sake. The real-world advantages are tangible:
Key Benefits of FHE in DAO Voting
-
Confidentiality of Votes: FHE ensures that individual votes remain fully encrypted and private throughout the voting process, protecting voter anonymity and reducing risks of coercion or manipulation. (Blockworks)
-

On-Chain Privacy with Public Verifiability: FHE enables votes to be cast and tallied on-chain without exposing individual choices, while still allowing the overall result to be publicly verified. (Zama fhEVM)
-
Elimination of Centralized Tallying Authorities: With FHE, vote tallying can be performed without a trusted third party, reducing centralization risks and enhancing DAO security. (Primus Labs)
-

Regulatory Compliance: FHE-based voting helps DAOs comply with data protection regulations by ensuring sensitive voting data is never exposed, supporting legal and governance requirements. (Fhenix)
-
Resistance to Frontrunning and Vote Manipulation: By encrypting votes, FHE prevents adversaries from seeing or acting on voting data in real time, mitigating frontrunning attacks and vote buying. (AGYSO ZK-DAO-VOTE)
- No Exposure of Individual Choices: Prevents retaliation or bribery based on vote history.
- No Frontrunning or Vote Buying: Eliminates the ability for attackers to manipulate outcomes mid-process.
- Regulatory Alignment: Helps DAOs meet emerging data protection standards globally (Fhenix compliance details).
- Censorship Resistance: Reduces central points of failure by distributing decryption authority across the community.
The result is a governance process where members can vote honestly with confidence that their decisions remain private, boosting legitimacy and participation rates across the board. As open-source tooling matures, expect confidential voting to become a baseline feature for serious DAOs rather than an optional add-on.
If your DAO handles sensitive proposals, treasury allocations, or controversial decisions, confidential voting is rapidly shifting from a “nice-to-have” to a competitive necessity.
The next generation of privacy-preserving DAO tools, built atop FHE, will power more resilient decentralized communities, where security and transparency do not come at the expense of individual privacy. The technology is ready; now it’s up to DAOs to execute.