Confidential voting has become a cornerstone of robust DAO governance, directly addressing some of the most acute risks in decentralized decision-making: voter coercion, manipulation, and privacy erosion. As DAOs mature and their treasuries and influence grow, so does the imperative to shield governance processes from undue external pressure and internal collusion. Market research and academic literature consistently highlight that private voting unlocks more honest participation and guards against corruption, ultimately strengthening the legitimacy of decentralized governance.
The Strategic Value of Privacy in DAO Voting
Public blockchains are designed for transparency, but this feature can backfire in governance contexts. When votes are visible on-chain before or during a proposal’s lifecycle, powerful actors may attempt to sway outcomes through bribery or intimidation. This risk is not theoretical; it is well documented in both traditional shareholder voting and emerging DAO ecosystems. By contrast, confidential voting mechanisms ensure that each member’s decision remains private until the tally is revealed, preserving autonomy and reducing the likelihood of groupthink or retaliation.
The demand for privacy-preserving voting is accelerating as DAOs handle larger treasuries and more consequential proposals. Recent frameworks, such as Semaphore and MACI (Minimal Anti-Collusion Infrastructure): demonstrate how advanced cryptography can combine privacy with auditability. These innovations empower DAOs to maintain open participation while protecting individual sovereignty.
Zero-Knowledge Proofs (ZKPs) for Confidential Ballots
The first pillar of modern private DAO governance is the use of Zero-Knowledge Proofs (ZKPs). ZKPs allow a participant to prove that their vote is valid, that they are eligible to vote and have not double-voted, without revealing any information about their identity or ballot choice. In practice, this means that ZKP-based systems like zk-SNARKs or zk-STARKs can verify vote integrity without exposing sensitive data. Leading frameworks such as Semaphore and MACI leverage these proofs to prevent vote tracing and collusion, offering both privacy for voters and verifiability for auditors.
This approach is especially valuable for DAOs with global membership who may face regulatory scrutiny or personal risk if their on-chain activity becomes public knowledge. ZKPs enable these members to participate confidently, knowing their choices remain shielded even from network validators or protocol operators.
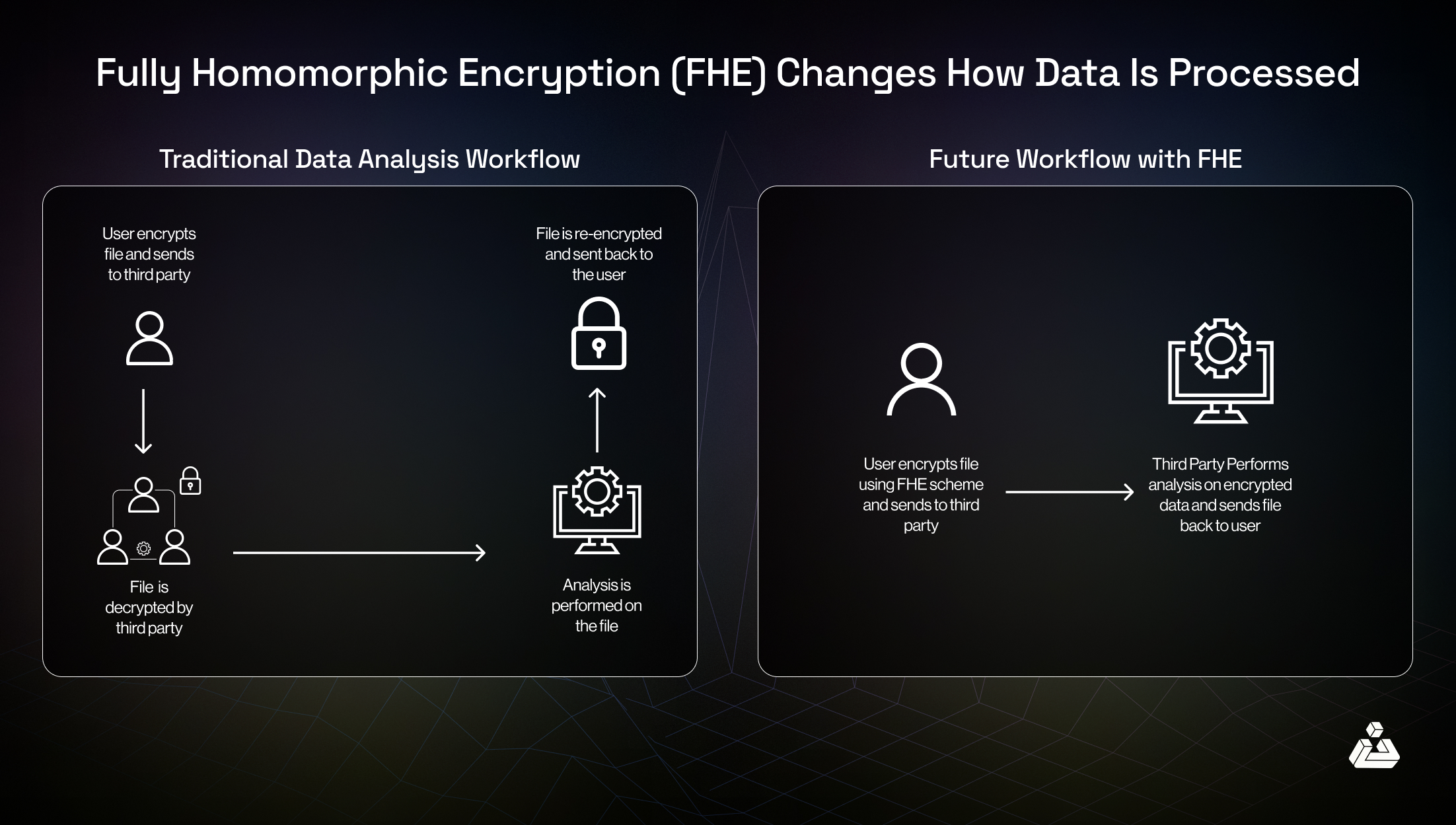
Homomorphic Encryption for End-to-End Encrypted Voting
The second major technology transforming confidential DAO voting is homomorphic encryption. Unlike traditional encryption schemes that require decryption before data can be processed, fully homomorphic encryption allows computations, such as vote tallying, to occur directly on encrypted ballots. Only the final aggregated result is decrypted at the end of the process, ensuring that individual votes remain secret throughout.
This method has gained traction in scalable DAO protocols like S2DV (Scalable and Secure DAO Voting), which provide robust confidentiality without sacrificing accuracy or efficiency. By enabling end-to-end encrypted elections on public blockchains, homomorphic encryption sets a new standard for privacy-preserving voting in blockchain governance.
- No single party ever gains access to raw votes, dramatically reducing attack surfaces.
- Tallies remain auditable, supporting trustless verification post-election without exposing voter intent.
- Scalability improvements address historic pain points around gas costs and on-chain computation limits.
The Emerging Best Practices for Private DAO Governance
Implementing these technologies requires more than technical integration; it demands strategic alignment with organizational values and continuous security assessment. Leading DAOs now follow best practices such as shielded voting periods (where no ballots are decrypted until after polls close) and regular audits of cryptographic infrastructure. Member education remains essential so that participants understand both their rights to privacy and how confidential mechanisms work under the hood.
Adopting zero-knowledge proofs and homomorphic encryption is not just a technical upgrade; it fundamentally redefines the trust model for DAOs. When governance processes are both confidential and verifiable, organizations can attract a wider spectrum of participants, including those for whom privacy is non-negotiable. This is particularly relevant in jurisdictions with uncertain regulatory environments or in DAOs managing sensitive assets and data.
Advanced Privacy Technologies in DAO Voting
-
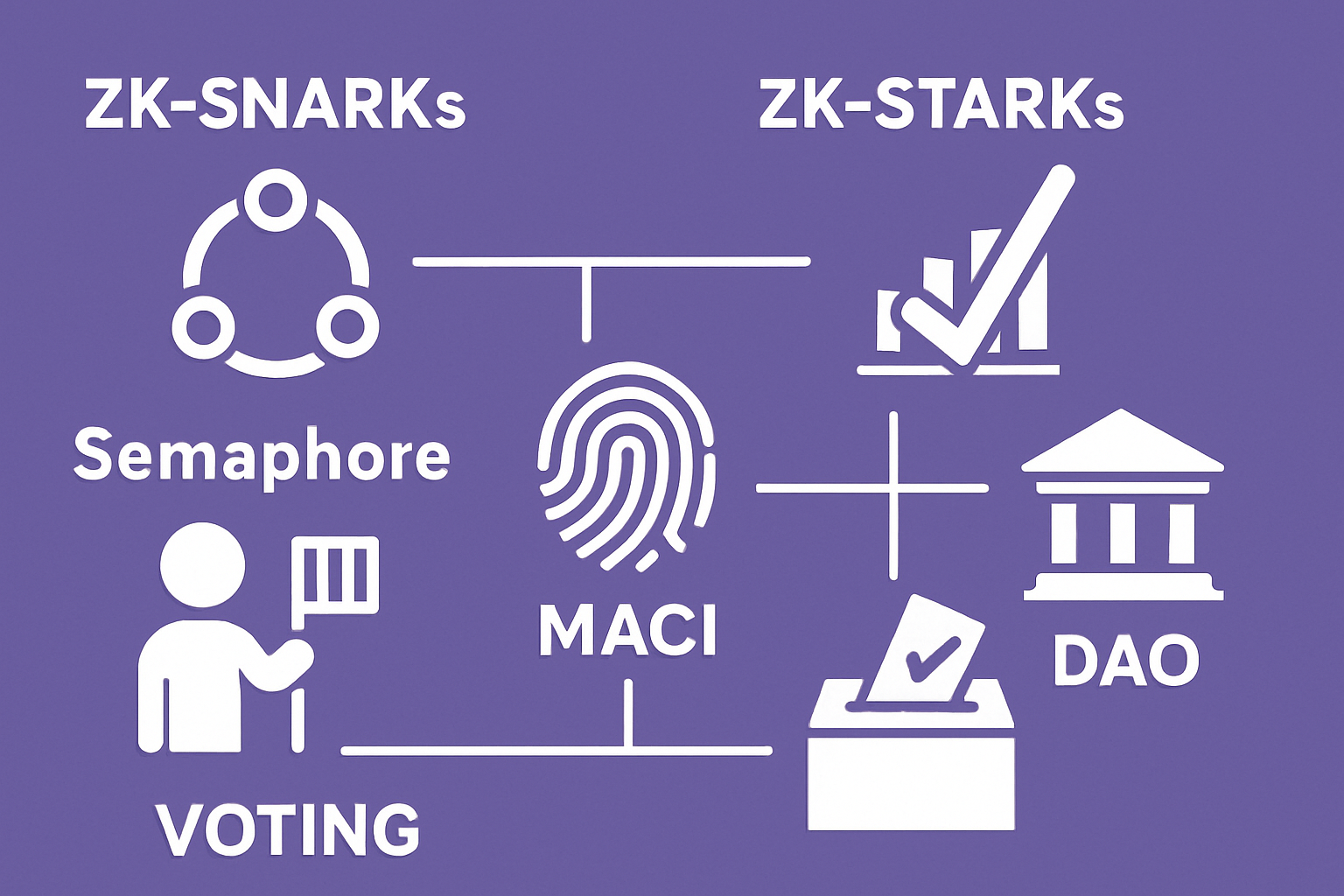
Zero-Knowledge Proofs (ZKPs) for Confidential Ballots: Implementing ZKPs, such as zk-SNARKs or zk-STARKs, allows DAOs to verify that votes are valid and counted without revealing individual voter choices, ensuring both privacy and auditability. Leading DAO frameworks like Semaphore and MACI (Minimal Anti-Collusion Infrastructure) leverage ZKPs to prevent vote tracing and collusion.
-
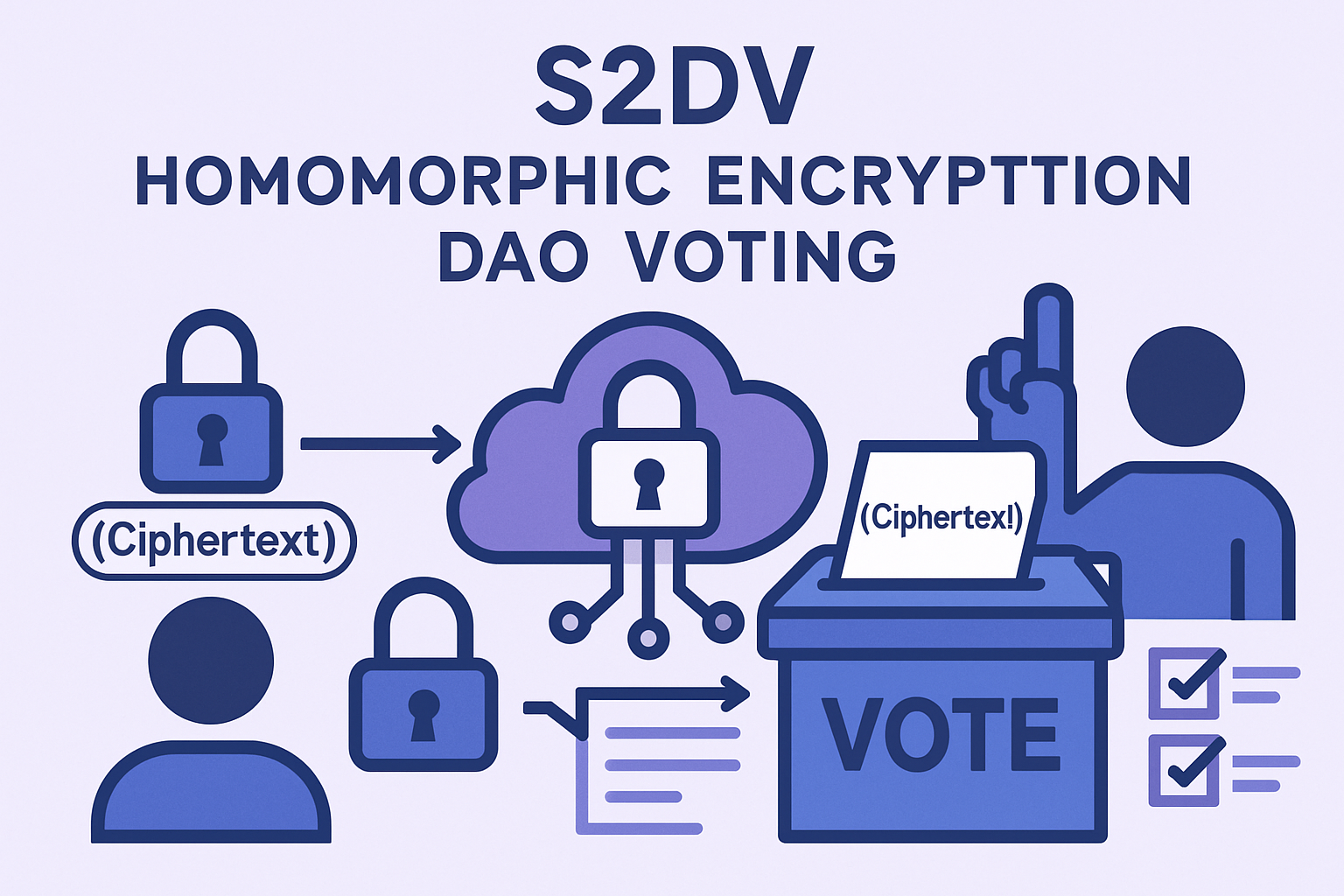
Homomorphic Encryption for End-to-End Encrypted Voting: Utilizing fully homomorphic encryption enables computations on encrypted votes, so tallies can be performed without decrypting individual ballots. This best practice is gaining traction in scalable DAO voting protocols (e.g., S2DV), providing robust confidentiality while maintaining the integrity of the overall election process.
To maximize the benefits of these cryptographic primitives, DAOs should:
- Integrate ZKPs at the protocol layer to ensure ballot secrecy by default. Projects like Semaphore allow anonymous signaling while maintaining Sybil resistance, making them ideal for token-weighted or membership-based voting.
- Leverage homomorphic encryption in all-stakeholder votes to prevent any party, including administrators, from accessing individual ballots. This practice aligns with the highest standards of end-to-end encrypted governance.
- Conduct regular cryptographic audits to assess resilience against emerging threats such as quantum computing or novel attack vectors targeting implementation flaws.
- Provide transparent post-vote verification tools, such as public audit trails powered by ZKPs, so members can confirm their participation without revealing their choices.
The operationalization of confidential voting also requires cultural adaptation. DAOs must invest in member onboarding and documentation that demystifies advanced concepts like zk-SNARKs or ballot aggregation under homomorphic encryption. By fostering literacy around these systems, communities can build durable trust and avoid the pitfalls of black-box governance.
Practical Impacts and Looking Ahead
The integration of zero-knowledge proofs and homomorphic encryption into DAO voting protocols has already begun to reshape what is possible for decentralized organizations. Early adopters report higher voter turnout rates and greater willingness among members to participate in contentious proposals, outcomes that directly correlate with increased privacy protections. As frameworks like Semaphore, MACI, and S2DV mature, we anticipate further improvements in scalability and user experience, paving the way for widespread adoption across diverse DAO verticals.
The next frontier will likely involve composable privacy layers that allow DAOs to tailor confidentiality settings based on proposal sensitivity or regulatory requirements. This modular approach empowers organizations to strike an optimal balance between transparency (for accountability) and privacy (for security), ensuring that decentralized governance remains both resilient and adaptable in an evolving threat landscape.
For DAOs seeking actionable guidance on deploying these solutions today, and understanding how they fit within broader security architectures, explore our dedicated resources on confidential voting system transformation and private voting protocols for confidential DAO governance.