In the shadowy realm of confidential DAOs, where governance hinges on anonymity and trustless execution, a single vulnerability can unravel the entire structure. Sybil attacks, those insidious maneuvers where one actor floods the system with fake identities, pose an existential threat to sybil resistance blockchain mechanisms. Imagine a governance vote swayed not by collective wisdom, but by a lone manipulator puppeteering dozens of pseudonymous accounts. This isn’t dystopian fiction; it’s the reality confronting builders of confidential DAO governance. As DAOs evolve toward privacy-centric models, the demand for privacy-preserving uniqueness proofs has never been more urgent, blending zero-knowledge cryptography with robust identity aggregation to safeguard democratic processes without sacrificing user sovereignty.
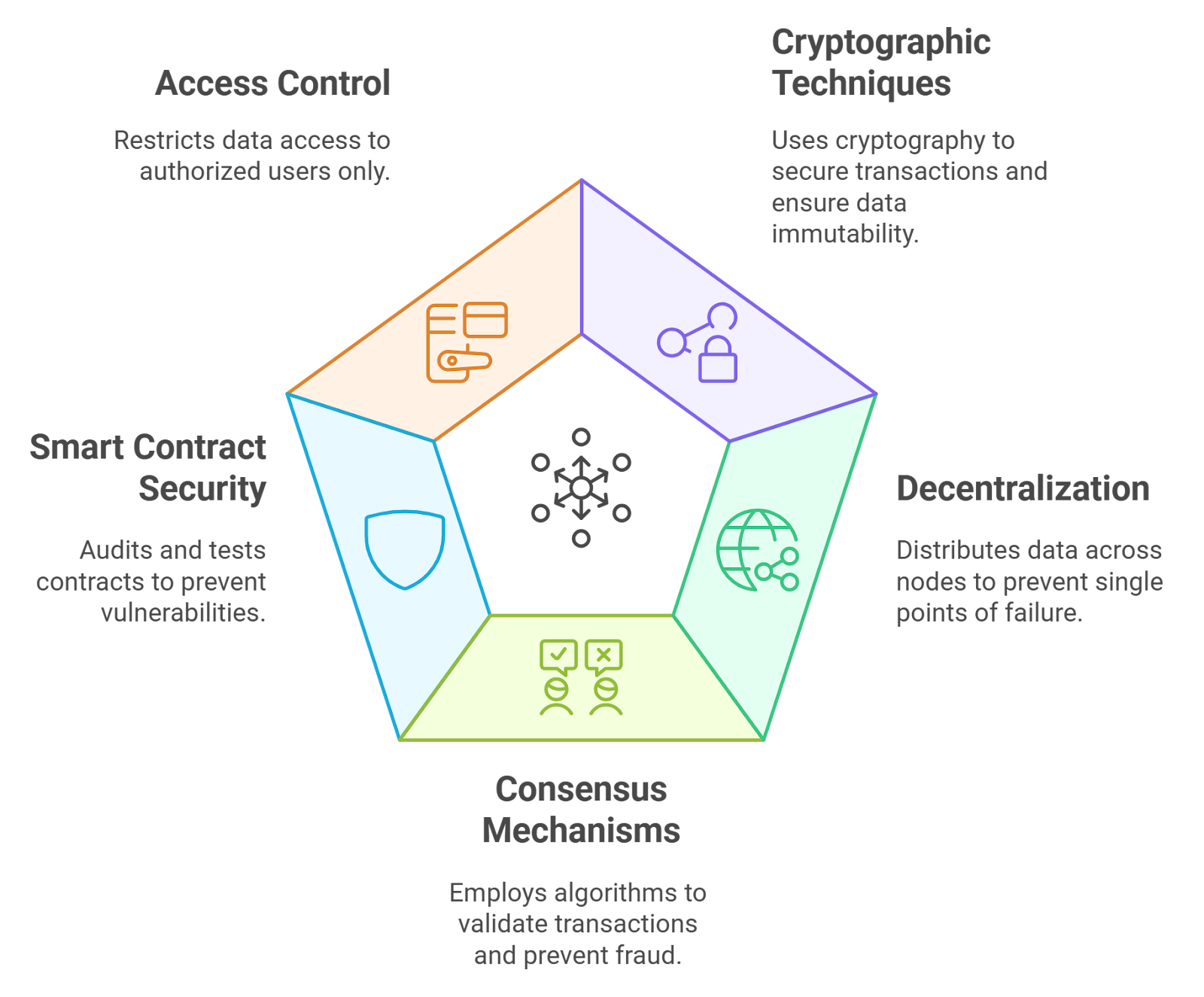
The Hidden Mechanics of Sybil Attacks in DAOs
Sybil attacks thrive in decentralized environments precisely because pseudonymity, a cornerstone of blockchain, lowers the barrier to identity proliferation. A single adversary crafts multiple nodes or accounts, amplifying their influence in voting, resource allocation, or consensus. In Web3 contexts, this manifests as vote rigging in DAOs or overwhelming airdrop distributions. Sources like TokenMinds and Colony. io underscore how these exploits target the pseudonymous nature of systems, allowing one person to masquerade as many.
Consider a confidential DAO coordinating high-stakes decisions on proprietary strategies. Without safeguards, an attacker could dominate proposals, diluting genuine member input. Historical precedents in networks like Nervos highlight how adversaries subvert functioning by controlling swaths of nodes. In confidential settings, the stakes escalate: leaked governance data could expose sensitive operations, compounding the breach with identity compromises as noted in idOS discussions on data breaches exposing millions of records.
Why Conventional Mitigations Compromise DAO Privacy
Traditional countermeasures falter under the weight of confidentiality demands. Token-weighted voting assumes aligned incentives, yet whales or sybil clusters can hoard or fabricate holdings. Proof-of-Personhood (PoP) schemes, while promising as in Polkadot’s zero-knowledge approach, often lean on biometrics or external verifiers, introducing centralization vectors antithetical to DAO ethos.
KYC mandates, touted by some for uniqueness, erode the very privacy that draws innovators to confidential DAOs. Users end up resubmitting sensitive documents across platforms, as idOS warns, inviting breaches that cascade through ecosystems. Even advanced consensus like Proof of Identity (PoID) with biometrics risks mass surveillance, clashing with the decentralized ideal. My 15 years navigating equity markets taught me that true resilience stems from layered, non-invasive defenses, not blunt identity mandates.
Core Limitations of Traditional Sybil Defenses
-
Privacy erosion via KYC: Requiring users to submit sensitive personal documents exposes data to breaches, where one incident can reveal millions of records, as warned by idOS.
-
Centralization from trusted verifiers: Dependence on centralized parties for identity checks creates single points of failure and contradicts DAO decentralization principles.
-
Scalability issues in ZK-constrained data structures: Zero-knowledge proofs struggle with complex data structures, limiting efficiency in large-scale confidential DAOs, per arXiv analysis.
-
Incentive misalignment in token systems: Token-weighted voting enables whale dominance or farming exploits, failing to enforce true one-person-one-vote equity.
-

Vulnerability to social engineering in PoP: Proof-of-Personhood mechanisms, like Polkadot’s, risk coercion or manipulation, undermining privacy-preserving uniqueness.
These pitfalls demand a paradigm shift toward solutions that prove uniqueness without revelation. Enter privacy-preserving uniqueness proofs, leveraging zero-knowledge proofs to affirm “one person, one vote” sans disclosure.
LinkDID and the Dawn of Sybil-Resistant Identities
LinkDID emerges as a beacon in this landscape, a decentralized identity protocol detailed in recent arXiv research. It aggregates identifiers into a privacy-preserving whole, enabling selective credential disclosure while thwarting multiplicity. Users prove uniqueness through cryptographic linkages, recoverable keys ensuring asset control post-loss, all without oracle dependencies.
Strategically, LinkDID aligns with confidential DAO needs by sidestepping external data, fostering self-sovereign identity. In governance, members generate proofs attesting to singular participation, audited on-chain yet opaque to observers. This mirrors idOS’s vision of ZK proofs atop secure data stores, extending sybil resistance to zero-knowledge DAO voting.
Proof-of-Social-Capital complements this, supplanting stake with verifiable social graphs. Through ZK and credentials, it quantifies influence from interactions, curbing sybil floods while incentivizing authentic engagement. ArXiv’s analysis reveals its equity boost, vital for DAOs where merit, not capital, should prevail.
Privacy-preserving credentials represent the next frontier, enabling DAOs to verify eligibility without exposing personal details. As outlined in emerging blockchain insights, these credentials underpin private voting systems and reputation accrual, fortifying sybil attacks DAOs defenses. Voters prove attributes like membership tenure or contribution history via zero-knowledge proofs, ensuring audits without traceability. This approach circumvents KYC pitfalls, preserving the anonymity essential to confidential DAO governance.
Integrating Uniqueness Proofs: A Strategic Roadmap
Deploying these technologies requires deliberate architecture. DAOs must embed uniqueness proofs into smart contracts, leveraging protocols like LinkDID for identity linkage. Governance modules then enforce proof submission before vote casting, with on-chain verification circuits confirming singularity. This setup demands thoughtful oracle minimization; self-sovereign models prevail by design.
Proof of Identity (PoID) offers another lens, granting equal voting power per unique human via biometric anchors and verification events. While potent for equity, it warrants caution in confidential contexts to avoid over-reliance on physical proofs. Blending PoID elements with ZK layers yields hybrid vigor, as seen in Polkadot’s PoP explorations.
From my vantage in global markets, where asymmetric information breeds exploitation, these tools echo disciplined risk management. They transform vulnerability into strength, ensuring governance reflects true stakeholder will.
Comparative Analysis of Sybil Resistance Strategies
Evaluating options reveals trade-offs in privacy, scalability, and adoption readiness. LinkDID excels in key recovery and oracle independence, ideal for asset-heavy DAOs. Proof-of-Social-Capital fosters organic growth through networks, suiting community-driven entities. Privacy-preserving credentials shine in modularity, integrable across chains.
Comparison of Sybil Resistance Methods
| Method | Privacy Level | Sybil Resistance | Centralization Risk | Use Case |
|---|---|---|---|---|
| LinkDID | High | Strong | Low | Asset Governance |
| Proof-of-Social-Capital | High | Medium-Strong | Low | Community DAOs |
| PoP/PoID | Medium | Strong | Medium | Equity Voting |
| Traditional KYC | Low | Strong | High | Regulated DAOs |
Confidential DAOs benefit most from layered stacks: base uniqueness via LinkDID, augmented by social proofs for nuance. This mitigates single-point failures, enhancing sybil resistance blockchain posture.
Challenges persist, notably computational overhead in ZK proofs and user onboarding friction. Yet advancements in recursive proofs and hardware acceleration erode these barriers. idOS’s data-centric ZK generation exemplifies scalable paths forward, shielding against breaches that plague repeated document sharing.
Builders must prioritize iterative testing, simulating attacks to validate proofs. Engage communities early, aligning incentives with proof issuance. In my experience, prosperity favors the patient architect, methodically layering defenses.
Armed with privacy-preserving uniqueness proofs, confidential DAOs transcend fragility. They embody resilient governance, where anonymity empowers rather than endangers. As Web3 matures, these innovations will define viable paths for decentralized coordination, securing collective prosperity amid pseudonymity’s promise.