Zero-knowledge proofs (ZKPs) are fundamentally reshaping the landscape of private DAO governance, offering cryptographic guarantees that were previously impossible in decentralized voting. As DAOs increasingly manage significant treasuries and sensitive decision-making, the need for confidential DAO voting solutions has become urgent. ZKPs offer a technical path forward, allowing participants to prove eligibility and cast votes without ever exposing their identity or vote choice on-chain. This is not just a theoretical advance – it addresses real risks like voter coercion, bribery, and manipulation that have plagued open blockchain voting models.
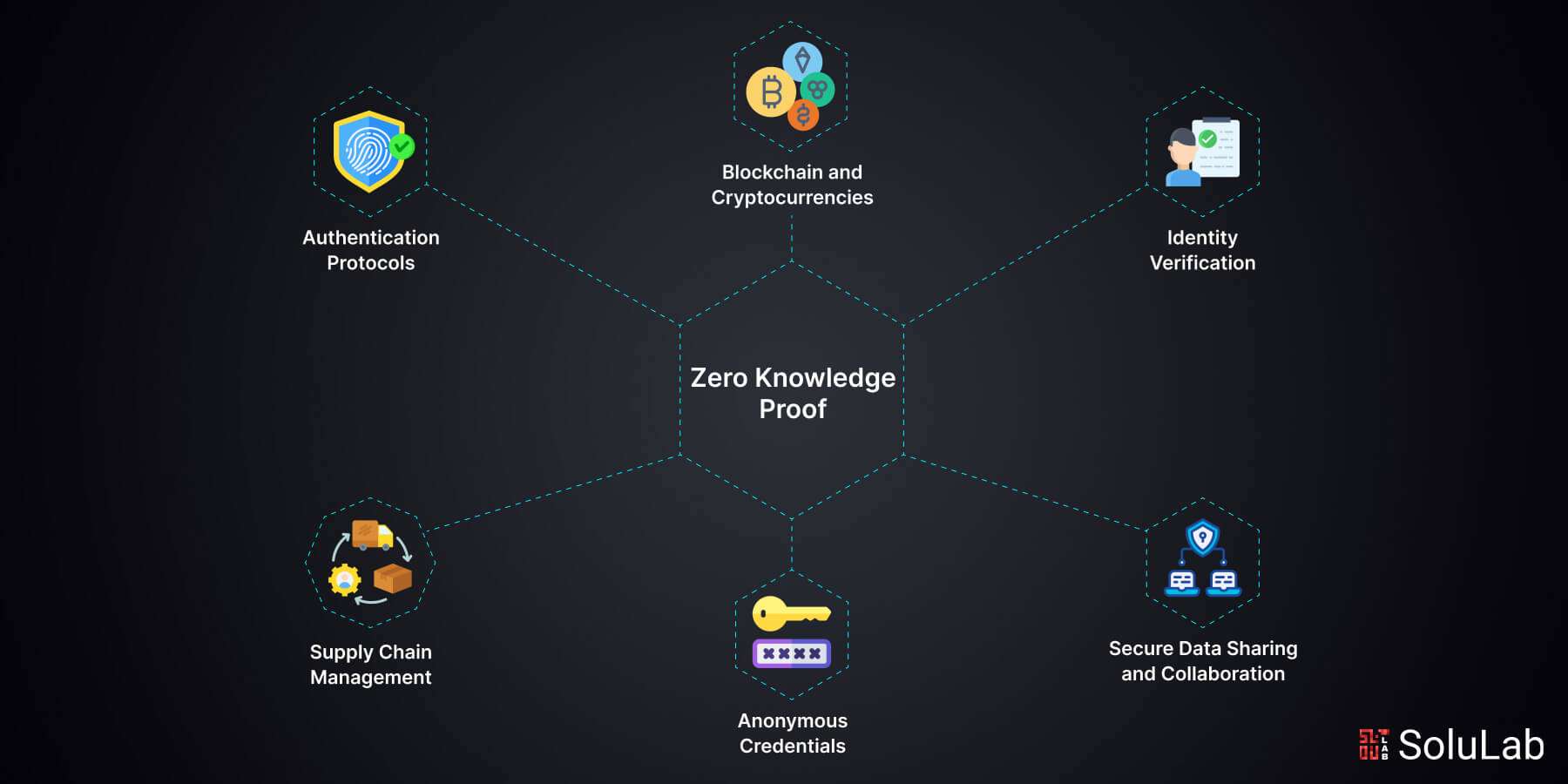
Why Privacy Matters in DAO Voting
The public nature of most blockchains means that every transaction, including votes, is by default visible to anyone. This transparency is a double-edged sword: while it enables auditability, it also exposes members to external pressure and undermines the core democratic values of many DAOs. Recent research from MIT and Ethereum privacy stewards highlights how open voting records can be exploited for vote buying or retaliation. By integrating zero-knowledge proofs for DAO voting, organizations can finally achieve both verifiability and privacy.
The Cryptographic Foundations: How ZKPs Enable Confidential Voting
ZKPs allow a voter (the prover) to convince the system (the verifier) that they meet certain criteria – such as holding a governance token or being on an allowlist – without revealing any other information. In practice, protocols like Semaphore use group membership proofs so you can prove you’re part of the DAO without showing which address you control. When combined with zk-SNARKs or similar constructions, these systems let users submit encrypted ballots that are later tallied using homomorphic encryption techniques. The result: individual votes remain secret while aggregate results are provably correct.
Projects like Shutter Network and Kite Protocol are already implementing these primitives in production environments, combining shielded voting with transparent result computation. This duality is critical: it ensures integrity while protecting the anonymity of each participant.
Step-by-Step Implementation Workflow for ZKP-Based Voting Dapps
Bringing these cryptographic concepts into live DAO infrastructure requires careful engineering:
- Development Environment: Start with tools like Node. js and Truffle for smart contract deployment; use Circom or ZoKrates for designing zk-SNARK circuits tailored to your governance logic.
- Smart Contracts: Develop contracts that enforce eligibility checks via ZKP verification rather than public whitelists.
- ZKP Circuits: Design circuits capable of validating encrypted ballots without leaking any vote data; this step is crucial for upholding confidentiality guarantees.
- User Interfaces: Build front-end applications that abstract away cryptographic complexity, letting users participate in confidential votes as easily as traditional ones.
- Testing and Auditing: Comprehensive test suites must simulate both honest and adversarial behaviors to ensure no information leaks through side channels.
This workflow not only protects voter privacy but also enhances organizational trust – a non-negotiable requirement as DAOs scale into more sensitive domains. For developers seeking deeper implementation details, see our technical breakdown at Implementing Zero-Knowledge Proofs for Confidential DAO Voting.
Integrating zero-knowledge proofs into DAO voting workflows does not come without challenges. Performance, scalability, and user experience are critical considerations. While zk-SNARKs and related technologies have matured rapidly, generating and verifying proofs can still be computationally intensive, especially for large-scale DAOs with thousands of members or multi-choice ballots. Developers must optimize circuit design and leverage efficient libraries to ensure voting remains fast and accessible.
On the UX front, abstracting away cryptographic complexity is essential. End users should never need to understand elliptic curve pairings or circuit constraints to participate in a vote. Instead, intuitive interfaces should guide users through eligibility verification and ballot submission with clear feedback at each step. The goal is for privacy-preserving voting to feel as seamless as traditional on-chain voting – just without the privacy tradeoffs.
Best Practices for Secure and Private DAO Voting
- Use well-audited ZKP libraries: Favor established tools like Semaphore, Circom, or ZoKrates that have undergone rigorous security reviews.
- Minimize on-chain data exposure: Store only encrypted ballots or ZKP hashes on-chain; avoid publishing any metadata that could deanonymize voters.
- Implement robust key management: Securely manage decryption keys for homomorphic tallying; consider threshold cryptography to distribute trust.
- Conduct external audits: Engage third-party security researchers to review both smart contract logic and cryptographic circuits before deployment.
The practical impact of these best practices is profound: they directly reduce the risk of voter deanonymization while ensuring that only eligible members can influence governance outcomes. As DAO treasuries grow and regulatory scrutiny intensifies, these safeguards are no longer optional – they are foundational to sustainable decentralized governance.
Example Circom Circuit for Eligibility Verification
Below is an example Circom circuit that verifies a voter’s eligibility using a Merkle proof. This allows the voter to prove they are in the set of eligible voters without revealing their identity.
pragma circom 2.0.0;
// This circuit checks if the voter's public key hash is in the Merkle tree of eligible voters
include "circomlib/merkleProof.circom";
// The depth of the Merkle tree (e.g., 16 for 2^16 leaves)
const TREE_DEPTH = 16;
component main {public [root, pubkeyHash]} = MerkleProof(TREE_DEPTH);
// Inputs:
// - root: Merkle root of eligible voters (public)
// - pubkeyHash: Hash of voter's public key (public)
// - pathElements: Sibling nodes for the Merkle proof (private)
// - pathIndices: Binary path indices (private)
//
// The circuit proves that pubkeyHash is a leaf in the Merkle tree with root 'root'.
This circuit can be compiled and integrated with a ZKP system, enabling private eligibility verification in DAO voting protocols.
The next wave of innovation will likely focus on interoperability between privacy-preserving protocols and mainstream DAO tooling. Projects like Shutter Network’s shielded voting layer for Snapshot demonstrate how confidential voting can be integrated into familiar platforms without sacrificing usability or transparency. Expect further advances in recursive ZKPs, enabling more complex governance processes (like quadratic voting or ranked-choice ballots) while maintaining strong confidentiality guarantees.
If your organization is considering a migration toward private DAO governance, start by mapping your requirements against available ZKP frameworks. Evaluate tradeoffs between proof size, verification speed, and integration complexity. For further technical insights on secure implementation patterns, review our advanced guides at Implementing Zero-Knowledge Proofs for Private DAO Voting Systems.
The Future of Blockchain Privacy Voting
The trajectory is clear: as ZKP implementation in DAOs becomes more standardized and user-friendly, confidential governance will move from niche experiment to industry norm. This shift will empower communities to make high-stakes decisions free from surveillance or manipulation – restoring the original promise of decentralized autonomy with modern cryptographic rigor.